rcFileScan Tool

I released a new tool today on the Red Crow Labs github ( https://github.com/redcrowlab/rcFileScan ) .
This tool scans and parses ELF binaries and provides basic information about them, including certain types of basic vulnerabilities. Some examples include:
- Security compile time options such as ASLR, DEP, NX, etc.
- Reads the symbol table to find the use of commonly vulnerable bad functions
- ELF File Section permissions
- The usage of weak crypto functions
Now there are a lot of other tools that can do a lot of the things rcFileScan can do, such as readelf, objdump, etc. But the reason I created it is that while I know the PE file format pretty well, I was less familiar with the ELF format so I thought building a parser would be a good way to learn more about it. The other reason was that I am incorporating this into a larger tool that can work on multiple file formats (PE, PDF, Office, JAVA) and I need something I control. I have quite a bit of it done, but its not ready for release yet. It will have a web frontend and a backend database for the storage and correlation of file details.
I also wanted to "shell out" as little as possible and implement a lot of it myself rather than just wrapping existing tools.
The larger tool will be useful for at least two applications that I can see right now:
- Malware sample correlation over time
- Files under test by our lab that are from different versions of hardware and software products will have their attributes stored and correlated / tracked.
In the course of building this tool I had to build two others to help in testing it:
- rcTestBin.ELF - A compiled binary that has many of the attributes rcFileScan looks for so that you can test it and see it working. One of the more interesting things was the creation of a custom ELF section.
- rcSectionMangler - Allows you to change the permissions on a ELF bin section.
Here's a screenshot of it working with some of the options:
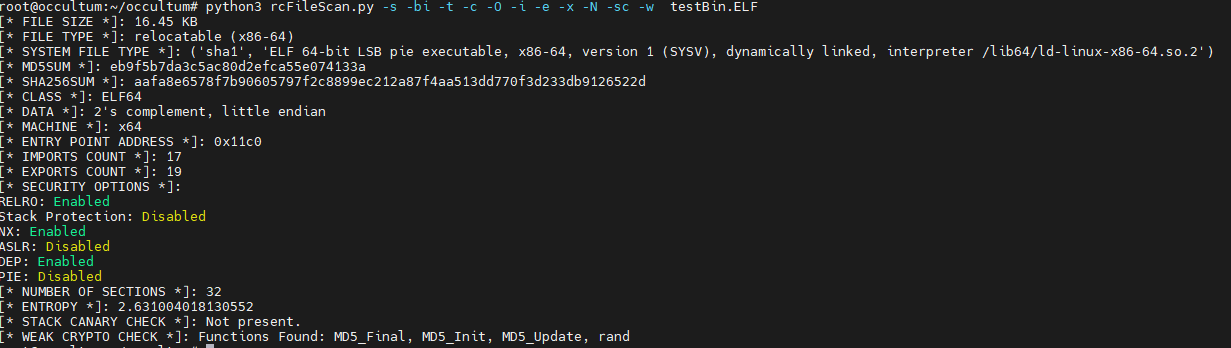
Imagine, we are testing 100s of different products and many of the files that come with these products, either extracted out of firmware, APKs, or just parts of the software package, and all of their information gets stored in the database.
Maybe we find a vulnerability in one of the files and then later we are testing a different version of the product and fine the same file, or similar attributes. Now we have a quick way to correlate this and identify the issue.
That's all for now, thanks for listening!
A.

