The Process
I'm a fan of some of Ray Dalio's thought processes from his Principles, to his concept of building "machines" within a business. At Red Crow Labs we have built a "machine" for our main service offering: Hardware Analysis.
Red Crow Labs have developed a standardized, repeatable, and in-depth process to evaluate hardware products from the point of view of a security attacker. This process can take several weeks or months, depending on the number and complexity of devices and the depth of the analysis required. The types of devices we look at:

- IoT
- OT / SCADA
- Medical Devices
- Avionics
- Automotive
- Scientific Instruments
- RF Communications Hardware & Mobile
- Sensors including space platforms
Overview of the Red Crow Lab Process
Each of the boxes below comprises a "Lab Station" where that part of the process is performed:
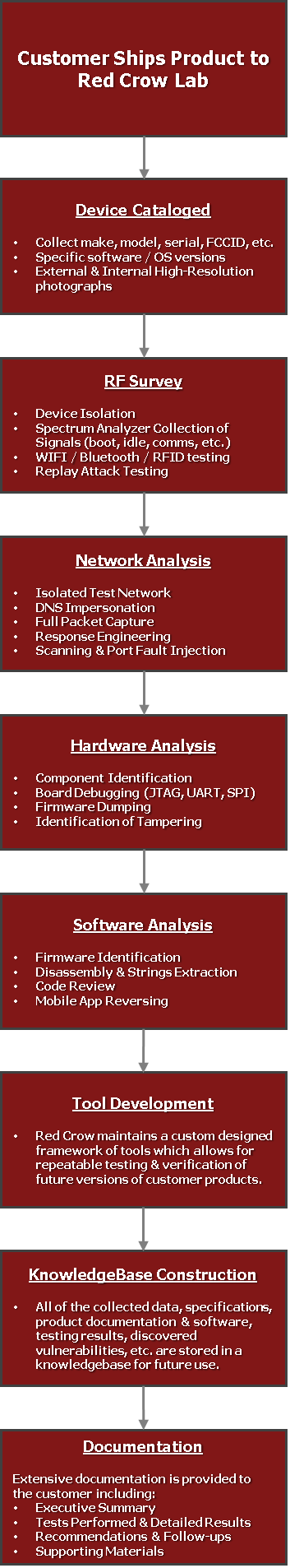
All of the instrumentation data is collected and stored to become part of the final deliverable package to the customer.
The Final Deliverable includes the following:
- Monthly or Weekly Status Reports
- Summary of tasks performed
- Planned tasks for next period
- Final Report Detailing:
- Executive summary including the "so what" and action items up front
- Lab stations used & instrumentation
- Device specifics and photographs
- Tests performed
- Results & Findings
- Analysis and supporting information such as screenshots, code snippets, steps to recreate attacks, etc.
- Recommendations & Remediations
- Our reports don't tend to contain much boilerplate. Reports are custom built for each project and it isn't unusual for a report to contain over 100 pages.
- Supporting Instrumentation Data
- Full packet capture files
- RF Survey data including images and signal .cvs files
- Interpreted scan results
- Collected documentation
- Logic analyzer and oscilloscope screenshots and data
- Firmware files, including extractions & disassemblies
- Internal & External High Resolution Photographs
- Secure Operating Certification Level (1-4)
- Project Presentation & Slides
Process Details
There are several additional details that are useful to note:
As a part of the network and software analysis we include protocol reversing and attack. Examples include sensitive information disclosure, MItM, replay attacks, etc. We will also attempt decoding communications when possible.
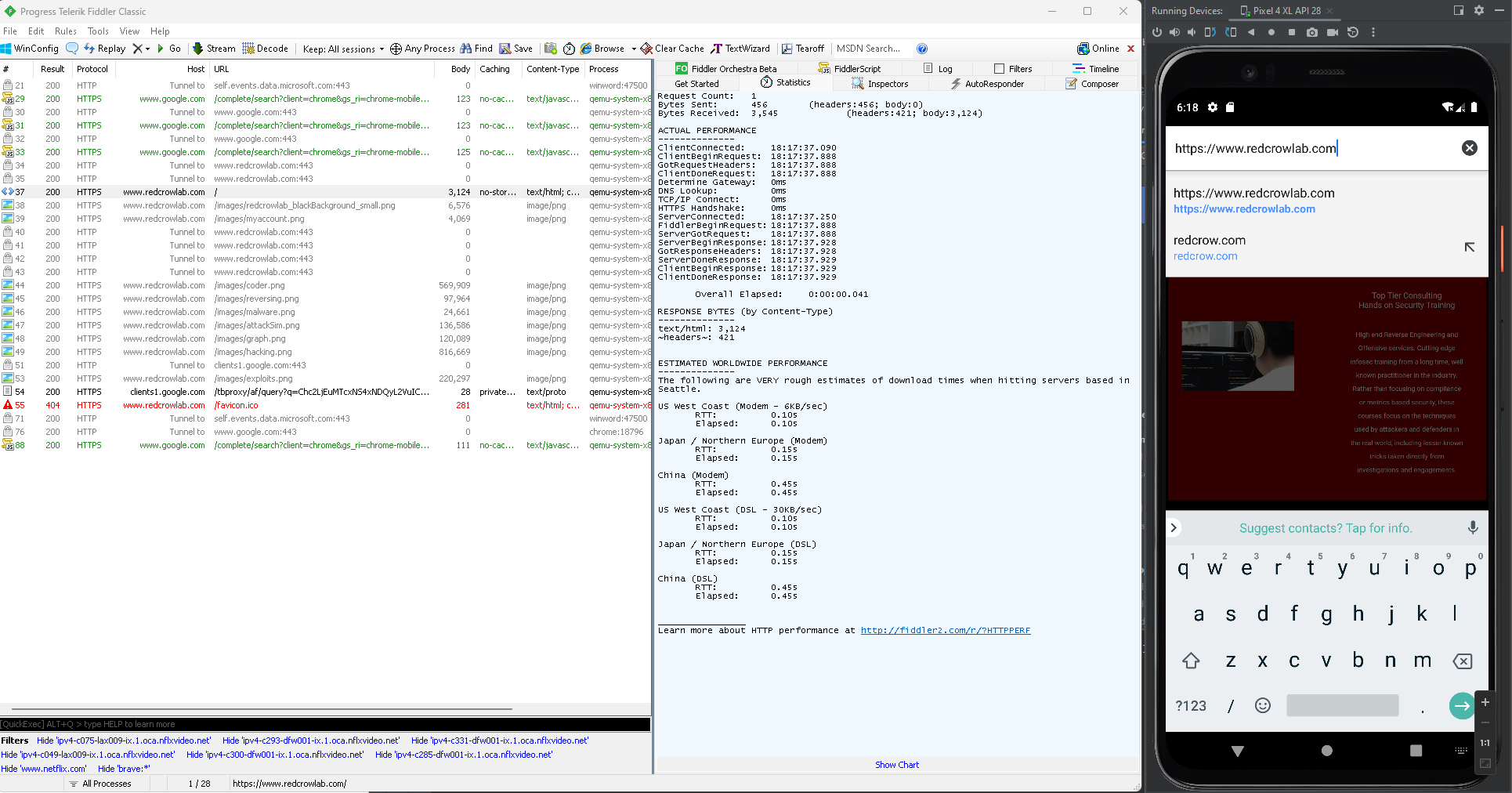
As a part of mobile app analysis we will attempt certificate de-pinning (if necessary) and sniffing / modifying communications between the device, the app and any web console interface that might be involved.
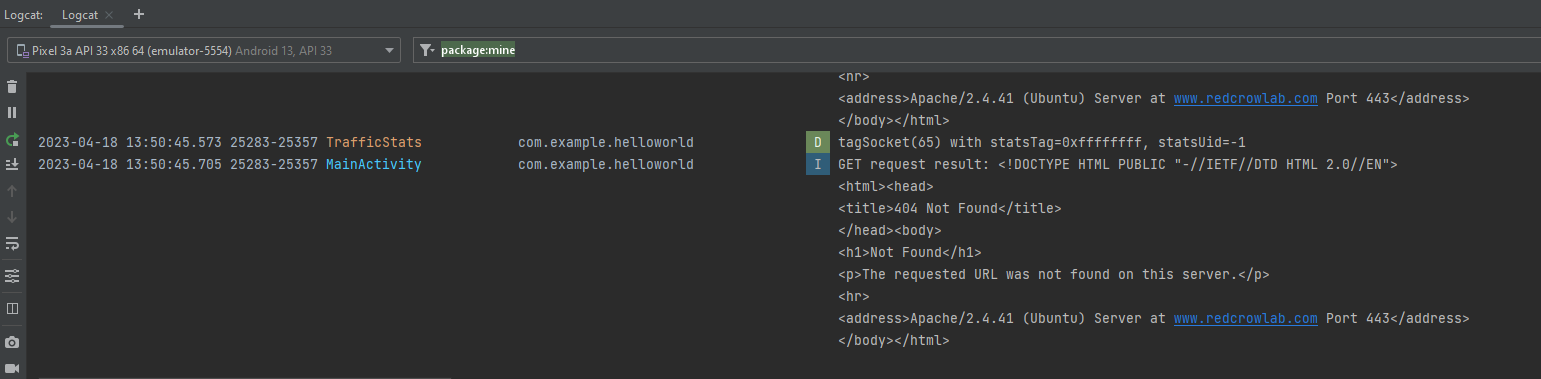
As a part of the hardware analysis we will attempt to identify PINs including voltages, grounds and signals using multimeters, oscilloscopes, and logic analyzers.

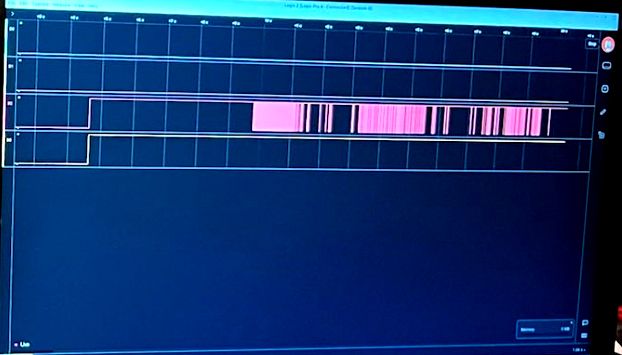
We will also identify specific components such as FPGAs, memory chips, CPUs, etc. as well as any associated vulnerabilities or attacks.
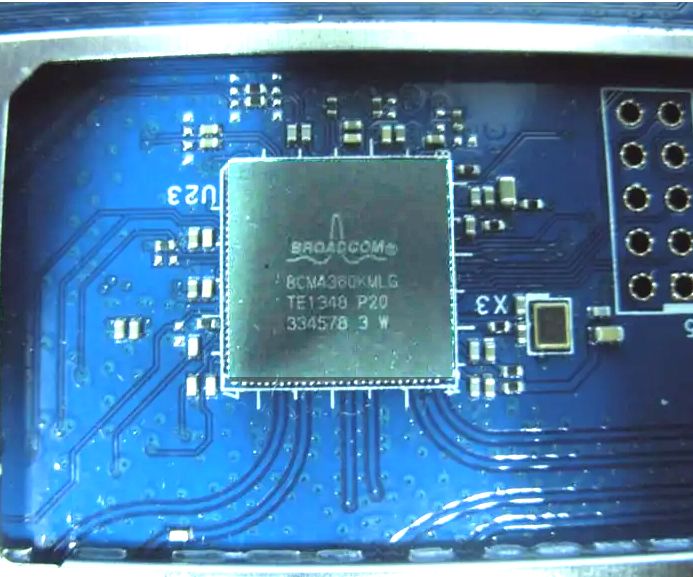
- Manufacturer: Broadcom Limited
- Product Category: WiFi Modules - 802.11
- Moisture Sensitive: Yes
- Product Type: WiFi Modules
- Protocol - WiFi - 802.11:WiFi
Frequency Range Power Output
2.412-2.462 GHz 2.4 GHz WiFi 770 mW
5.18-5.24 GHz 5 GHz WiFi 22 mW
5.21 GHz 5 GHz WiFi 48 mW
5.775 GHz 5 GHz WiFi 460 mW
As a part of the RF survey we can test near field and unintended emissions which can be used for side channel attacks, data exfiltration, etc. and include that data in the report.

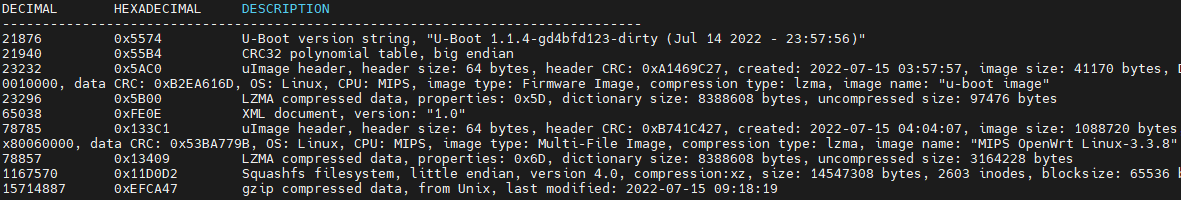
As a part of the firmware analysis we identify and extract firmware, analyze the files, pull out file systems such as squashfs, and reverse engineer relevant binaries. The following example shows the extraction of the files within a TP-Link WiFi router firmware:
Within the firmware file system is a custom written server compiled into an ELF binary which we disassemble and visualize its call graph:
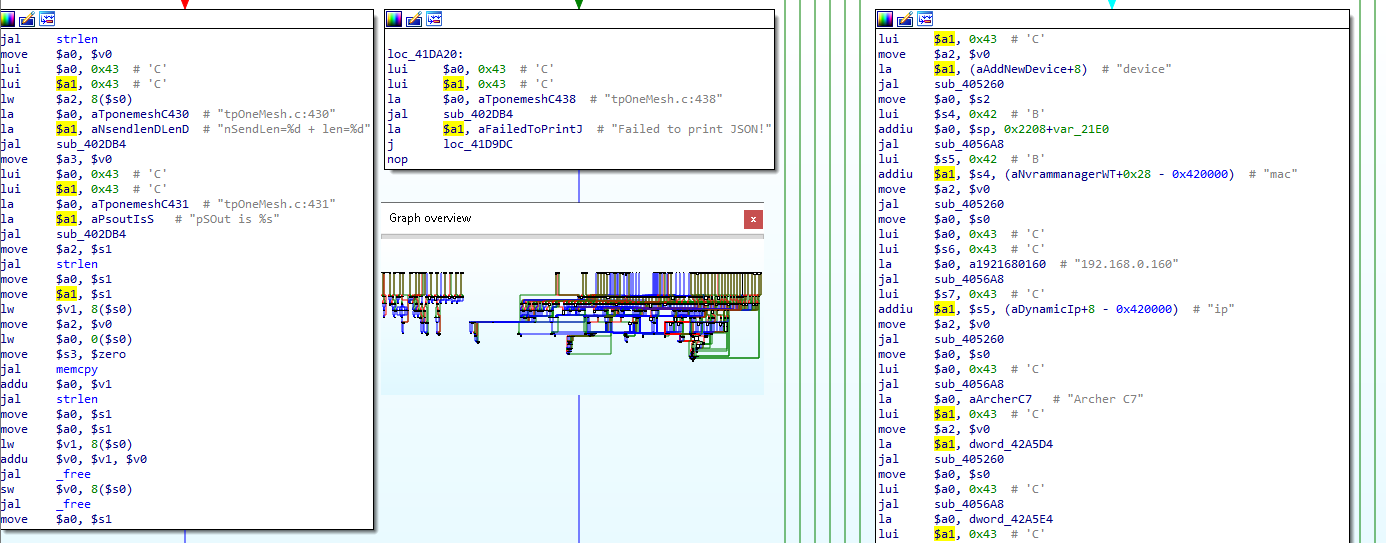
Custom attack tools and procedures are often developed and provided to illustrate the impact of issues discovered during the assessment. This might include a command and control binary compiled to operate on an embedded platform, specially crafted network packets to create effects on the device, or specific configuration changes that enable malicious actions.
Every step in this process is driven similar to a well managed code development environment, which each project having its own Git Repo, each task created as a GitLab issue, tracked and managed in a KanBan Board, and well documented in our internal collaboration system.
Customer data is encrypted and role based access controls implemented to protect these potentially sensitive results. Access to this data is audited and tracked.
I am unaware of other organizations providing this level of service other than internal test labs so if you are building a computing device for mass distribution, consider an assessment by Red Crow Labs.
Thanks for listening,
A.

