The Reality of Hacking OT/ICS/SCADA

There is a lot of discussion about critical infrastructure security these days. Some of us have been looking at this problem for over 20 years, especially the issue of nation states infiltrating each other's infrastructures using cyber-attacks. The media and politicians are finally starting to catch up and notice what has been a long running issue.
Recently Wired put out an article about Chinese hackers having infiltrated US critical infrastructure. (https://www.wired.com/story/nsa-china-hacking-criticial-us-infrastructure/)
This article talks about Volt Typhoon, an OT system hacking group assumed by be operating out of China.
“We think Volt Typhoon is doing this for espionage-related activity, but in addition, we think there’s an element that they could use it for destruction or disruption in a time of need,” Microsoft’s Ng said on Thursday.
Lets contrast this with an article Wired put out a little over 10 years ago:
Here is a quote from the author of this article showing how attitudes have changed:
"If it’s so easy to turn off the lights using your laptop, how come it doesn’t happen more often?" Michael Tanji, former intelligence officer. (https://web.archive.org/web/20230209050418/https://www.wired.com/2010/07/hacking-the-electric-grid-you-and-what-army/)
He goes on to talk about how the complexity of these systems and their use of proprietary operating systems are not available for your average hacker, and attacking them much more difficult than using Metasploit. That these systems are rarely connected directly to the public internet, making gaining access challenging.
Many people still have this attitude today, so lets explore this and see if we can come to some ground truth.
One quick comment I will make is that I have personally seen custom versions of Metasploit designed specifically for attacking OT/ ICS/SCADA type systems. So if it is so easy to turn off the lights using cyberattacks, why doesn't it happen more often?
There are a few concepts that are important to understand:
- Strategic Weapons
- Cascading Effects
- Unexpected or Unintended Trusts
STRATEGIC WEAPONS

Certain cyberweapons could be considered strategic, which means:
- One Time Use: These weapons may be "one shot" use, meaning once its launched, it has its affect, and then it can't be used again, therefore, you don't want to waste the capability. Its use induces a high motivation to fix the vulnerabilities that enabled the attack.
- Expense: Some estimates put the cost of Stuxnet into the tens of millions of dollars. While this may not compare to the cost of a modern jet fighter, missile, or nuclear weapon, cyber budgets are significantly smaller and so the relative impact is similar.
- High repercussions: Several nations have or are working on military retaliation policies for critical infrastructure attacks making the repercussions for using one extremely high.
- Cascading Effects: These attacks are most effective when coupled with cascading effects. Imagine you have a major natural disaster, then the power grid goes down, then the cell infrastructure goes down, then first responder comms are unavailable. Next, an enemy invades. How much more effective is that than just turning the lights off?
CASCADING EFFECTS
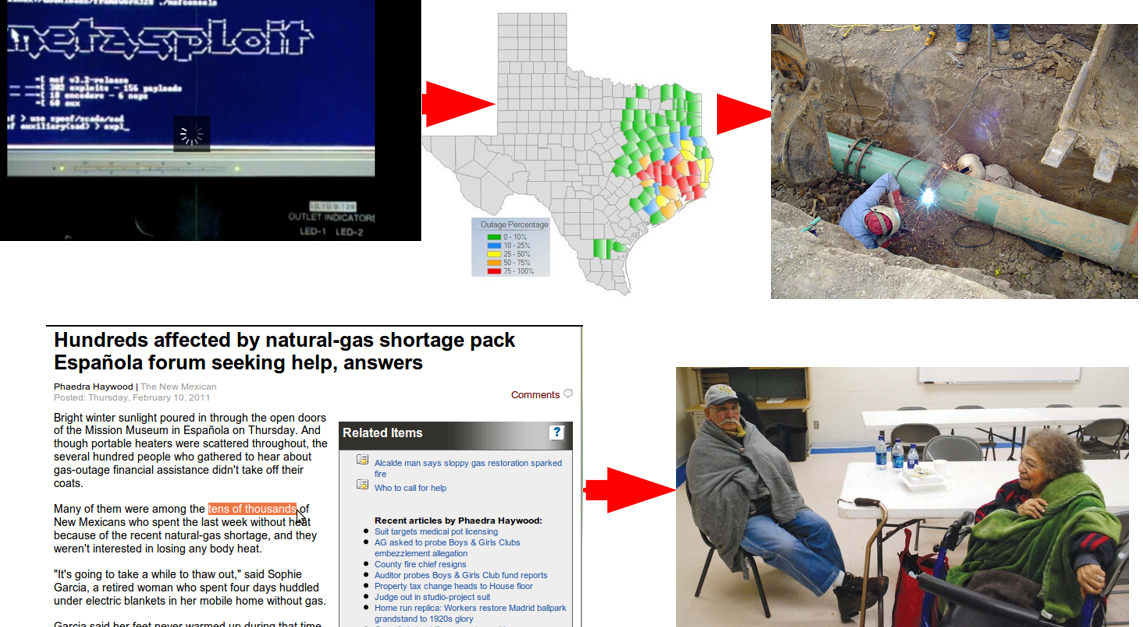
Real World Cascading Effects: An ice storm in east Texas affects the power to a natural gas network. This in turn causes a heating fuel shortage in northern NM, which in turn results in a large number of people being displaced and requiring assistence from local government.

It is very possible to replace "ice storm" with "metasploit attack" and have the same effect.
UNEXPECTED TRUSTS
Many people believe that these critical systems are protected by things like air-gaps (systems that are not connected to a public network like the internet), esoteric operating systems, and complexity. Often times even the organizations themselves that run these systems have these beliefs. Unfortunately, this is often not the case.
Many critical infrastructure organizations are short staffed when it comes to IT and cyber-security expertise and are highly incentivized to prioritize uptime over security. This leads to the creation of connections between corporate and OT networks to get the job done, but which offer opportunities to attackers.
Lets take a real world case study from a plant I assessed a number of years ago. First, I did a basic recon of the target. I drove around the public roads near the target facilities, examined them with google earth, took a look at their public footprint, etc.

I found a small building across the street that was essentially deserted, with no locks, a disabled alarm, no guards, etc. It was used periodically to train new employees in batches once a week or so. On this day, no one was there.

I went in and walked around, didn't see any security cameras and most of the building was open. I found several wiring closets and network ports / gear open and available:

I went ahead and plugged into the network and discovered I was on the companies main network. It took about 30 minutes or so to have domain admin. I won't go into the IT vulnerabilities here, but it was standard stuff, misconfigurations, weak passwords, etc. I mapped out the domain and looked for group names that might have something to do with the OT systems.
Eventually I managed to get onto an engineer's desktop which was full of information. He had manuals and how to's for most of the OT systems in use at the plant. Now, I'm not an electrician, plumber, or engineer of these types of systems so finding this desktop was fantastic for me as an attacker. I could read these documents at my leisure and gain some understanding of the most advantages things to attack to cause the most damage. In one of these documents I found a network diagram for their OT network, which I have redacted here to protect the customer.
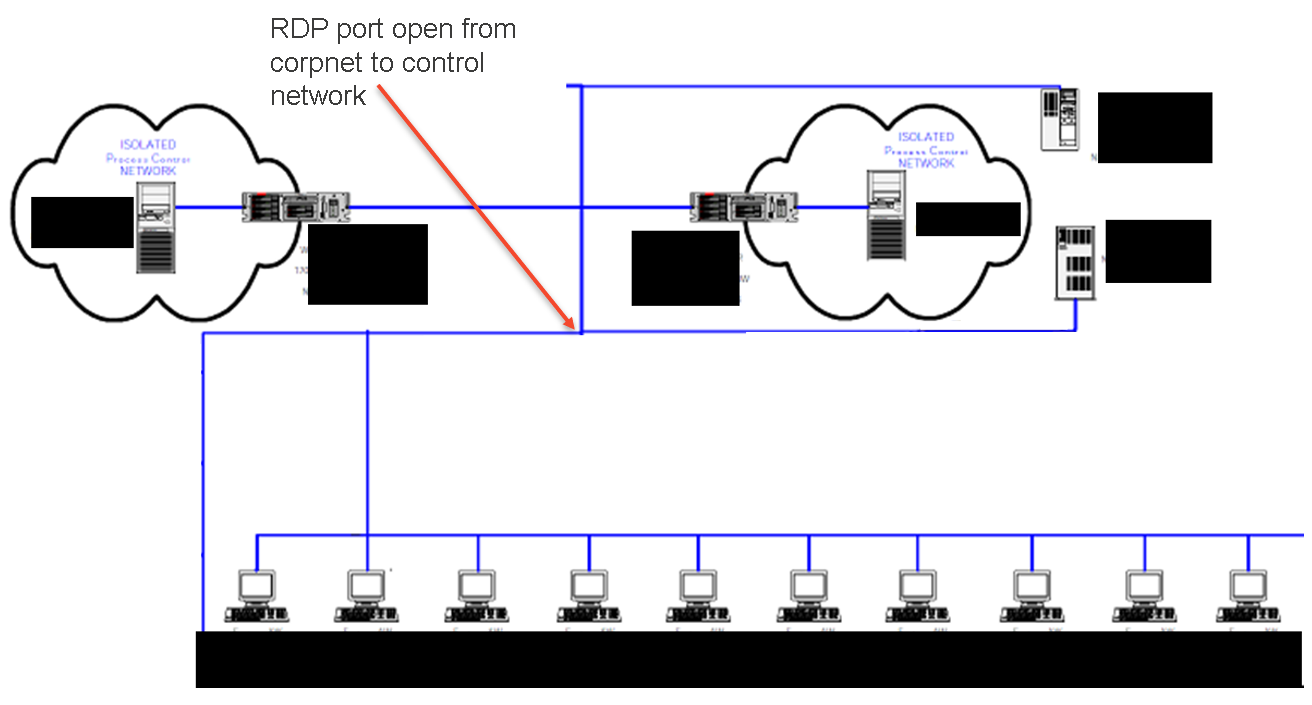
I noticed that even though it was labeled with ISOLATED or Air Gap, there was an RDP port open from the corporate network to the OT network. The engineer I had compromised had access to this RDP port and often left the connection up all day. I looked at their outlook calendar and identified when I would have a period of time when they weren't at their desk. I injected VNC into the desktop so I could have full GUI control and when they left, I went directly in to their OT network. Here are a few of the screens I was able to access and manipulate:
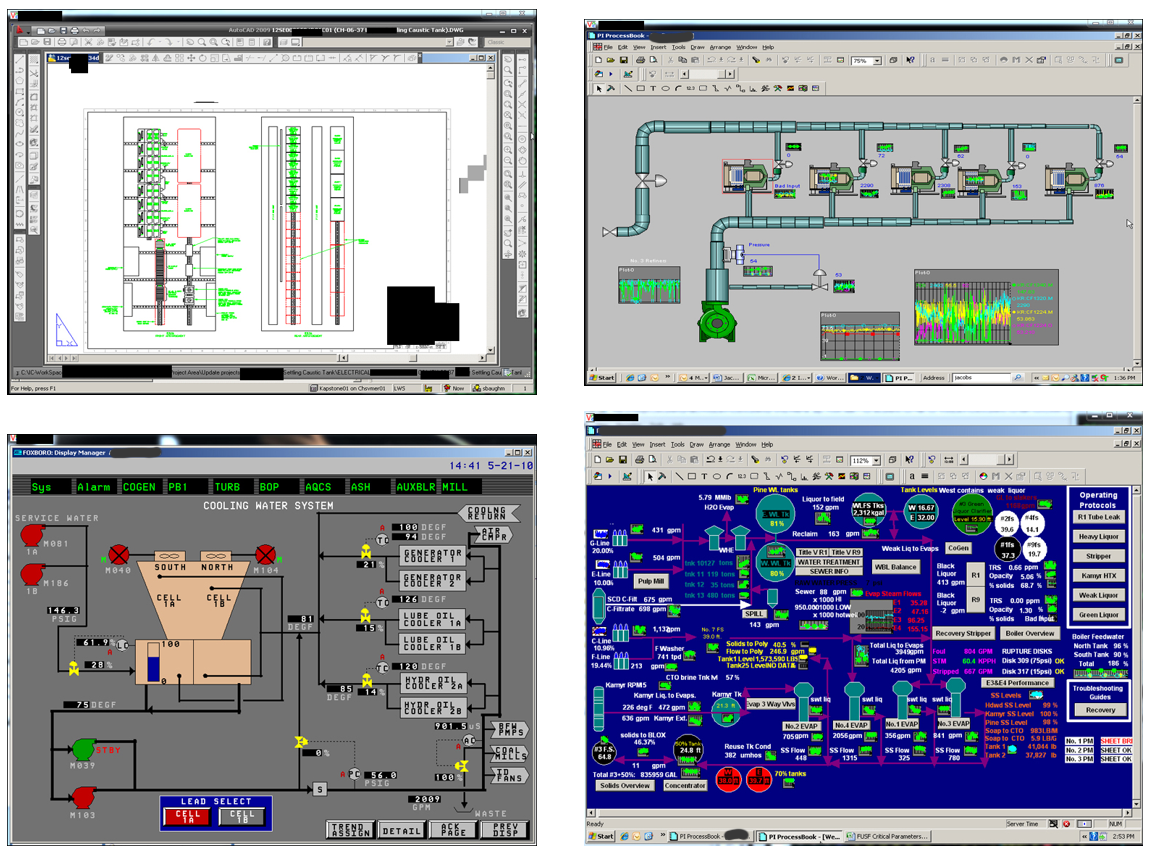
Eventually I was able to gain VPN access to the corporate network from my hotel room, and then jump from there to the OT network using the same approach.
Most of the OT systems were "air gapped" except for a gateway host through which the engineer could monitor and make changes to them. Most of the systems were complex and running operating systems and applications I hadn't seen before. However, all I had to know how to do was compromise corporate IT windows systems and jump through existing connections like RDP. I was able to read enough from the available manuals to cause real havoc had I been a bad guy.
In 2018 DHS released a report discussing Russian attacks into the US Electric Grid. (https://www.utilitydive.com/news/russian-hackers-infiltrated-utility-control-rooms-dhs-says/528487/)
If I was able to achieve the level of access and capability I demonstrated above, acting alone, with little funding, and with one day of work, what have the offensive cyber programs of our nations adversaries been able to accomplish?
Thanks for reading,
A.

