The Truth About TikTok - Part 1

This post provides a detailed analysis of TikTok on android and many of the steps and techniques that were used to examine the application. The goal of this post is to enable users to be better informed about what apps such as these are doing on their mobile devices.
First, a comment about Security Research. Security Research has gotten very quiet in recent years. I think this has happened because there is such a need in industry and most researchers are employed (captured) by organizations and focused inward. Because its valuable and there is a market for it so there is less reason for it to be given away.
What used to happen was a researcher would:
1.) Pick a vendor with a product that had wide adoption.
2.) Analyze the product and find its issues.
3.) Do a service to the consumer and publish the research so users could make decisions about the products they use.
4.) Do the vendor a service and provide them free, (albeit public) QA.
You had the David Litchfield's publishing about Oracle. The l0pht publishing about Microsoft. RainForestPuppy covering the web app world. Mike Lynn and Cisco.
In the early days this dynamic was adversarial, many times the vendor going after the researcher, or the researcher publicly ridiculing the vendor. But things evolved and the best vendors (Microsoft for example) learned to appreciate and work with the researchers, encourage them. Bug Bounties emerged. Researchers became more professional.
Now its time for Security Research to evolve once again. Where once we released 0days, now we need to release the internals of how these apps affect privacy. Where once we showed how products could accidentally expose our data through vulnerabilities, now we need to show how products manipulate our data and our opinions through algorithms and machine learning. Tech companies are now the ones hacking users.
The best friend you can have is the one who can be openly critical of your mistakes, without malice or derision, to help you improve. Its time Security Research resumed its role.
The best thing that companies who produce social media and other applications can do to serve their users is to encourage this sort of analysis, support it, and even do it themselves and release the results openly..
The conclusion upfront: TikTok has the ability to perform actions many would deem undesirable from a privacy or security standpoint. However, it doesn't appear to be any worse in this area than any other social media app. During the course of this analysis, TikTok was not observed doing anything that stands out as particularly nefarious (this doesn't mean that it couldn't/doesn't, just that it wasn't observed doing so.)
Now, having the ability to record video, audio, GPS location, interact with other apps, storage, re-write URLs, read and write from local storage, determine if you are using a VPN/Proxy, etc. are actually scary from a privacy point of view. However, most modern social media apps do the same. Its possible this analysis may be eye opening for some people who didn't realize the apps on their phone were doing all of these things.
WHAT WAS ANALYZED
The APK was downloaded from: https://tiktok.en.uptodown.com/android/download
Filename: tiktok-29-1-16.apk
File Size: 229382482
MD5SUM: d50792821f79035c31e2d4218ad91dc8
"com.zhiliaoapp.musically",
"2022901160",
"29.1.16"
This app was run on both a variety of emulators including Genymotion and Android Studio, as well as physically on an unlocked, but not rooted Samsung A21 running Android 12. The next chapter of this analysis will be done on a rooted device in order to gain access to more information.
ANALYSIS METHODOLOGY
Several steps were undertaking to analyze this app. These include:
- Extracting the APK and reviewing / decompiling files within manually.
- Decoding the APK with APK tool in order to view AndroidManifest.xml and other files.
- Scanning with automated tools such as MobSF.
- Using Android Studio's suite of debugging tools such as LogCat, Profiler, etc.
- The installation of custom SSL certificates and attempts to intercept SSL data.
- The use of Burp Suite and MITMProxy Web to intercept traffic.
- Attempts to remove certificate pinning and anti-debugging measures from the APK in order to gain better visibility into the apps behavior.
- Full network packet capture.
- Attempts to use debugging tools such as Frida (in this instance root was unfortunately required which prevented it)
- An open-source analysis of all the hosts / IPs the app contacts.
- Review of app permissions
- Code & API analysis
ANALYSIS CHALLENGES
There were a number of challenges to analyzing this app. These include:
- The app uses certificate pinning and has some additional checks which made it much harder to intercept traffic coming from the app.
- The app is set as non-debuggable which impeded the ability to watch what the app was doing inside of Android Studio.
- Secured memory management and other shared objects used by the app:
- The app had some protections against memory corruption attacks such as NX bit set, Stack Canaries, etc.
- Several fortified functions were used (memset, memcpy, strchr, etc.)
- The symbols were stripped.
- The app didn't seem to want to run at all in an emulator.
- Size: Its a large app and some analysis tools had problems loading it. There were several iterations of apk-mitm runs with larger and larger machines trying to operate on the apk without running out of memory. Trying to generate and view androguard call graphs failed miserable even on a machine with 64gb of ram.
- The use of strange Class and Method names such as:
LJ/N;->MaSOyuXL
ANALYSIS RESULTS
NETWORK CONNECTIONS
The geographic locations that the TikTok APK is configured to connect to can be seen on this map:
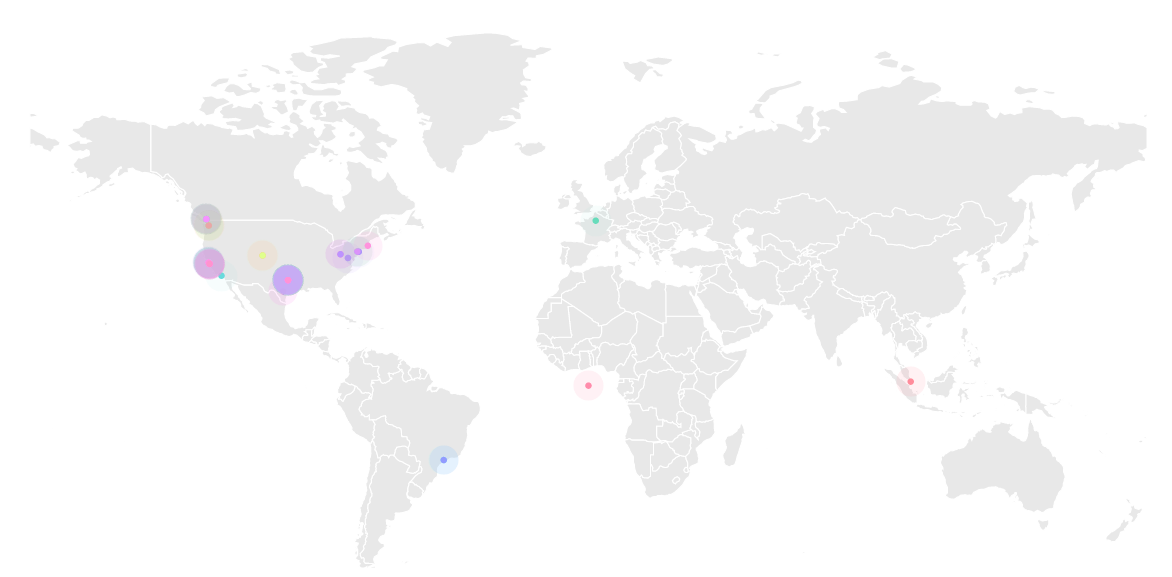
The hosts the app was seen to contact are:
xmlpull.org IP: 185.199.111.153 Country: United States of America Region: Pennsylvania City: California
www.webrtc.org IP: 142.250.69.238 Country: United States of America Region: California City: Mountain View
www.w3.org IP: 104.18.23.19 Country: United States of America Region: California City: San Francisco
www.tiktokv.com IP: 23.47.48.145 Country: United States of America Region: Texas City: Dallas
www.tiktok.in IP: 23.222.241.55 Country: United States of America Region: Texas City: Dallas
www.tiktok.com IP: 23.201.195.217 Country: United States of America Region: Texas City: Dallas
www.resso.com IP: 23.220.102.27 Country: United States of America Region: New Jersey City: Morristown
www.oasis-open.org IP: 172.99.100.168 Country: United States of America Region: Texas City: Windcrest
www.dns-sd.org IP: 96.76.212.165 Country: United States of America Region: California City: San Francisco
webcast.us.tiktokv.com IP: 23.201.195.207 Country: United States of America Region: Texas City: Dallas
webcast.tiktokv.com IP: 23.221.22.11 Country: United States of America Region: Texas City: Dallas
webcast-normal.tiktokv.com IP: 23.222.241.59 Country: United States of America Region: Texas City: Dallas
wa.me IP: 157.240.28.51 Country: United States of America Region: Colorado City: Denver
verify-sg.byteoversea.com IP: 23.47.48.151 Country: United States of America Region: Texas City: Dallas
verification-va.byteoversea.com IP: 23.47.48.154 Country: United States of America Region: Texas City: Dallas
verification-va-useast2a.byteoversea.com IP: 23.221.22.27 Country: United States of America Region: Texas City: Dallas
vcs-va.byteoversea.com IP: 23.222.241.41 Country: United States of America Region: Texas City: Dallas
vcs-va-useast2a.byteoversea.com IP: 23.221.22.15 Country: United States of America Region: Texas City: Dallas
vcs-sg.byteoversea.com IP: 23.222.241.37 Country: United States of America Region: Texas City: Dallas
upload.ffmpeg.org IP: 213.36.253.119 Country: France Region: Ile-de-France City: Paris
tools.ietf.org IP: 104.16.45.99 Country: United States of America Region: Texas City: Dallas
tiktokv.com IP: 23.221.212.64 Country: United States of America Region: Massachusetts City: Cambridge
tiktok.tiltify.com IP: 104.22.55.83 Country: United States of America Region: California City
support.tiktok.com IP: 23.47.48.150 Country: United States of America Region: Texas City: Dallas
sf16-va.tiktokcdn.com IP: 23.58.146.79 Country: Canada Region: British Columbia City: Vancouver
sf16-sg.tiktokcdn.com IP: 23.58.146.82 Country: Canada Region: British Columbia City: Vancouver
sf16-scmcdn-va.ibytedtos.com IP: 23.58.146.88 Country: Canada Region: British Columbia City: Vancouver
sf16-scmcdn-useast2a.ibytedtos.com IP: 23.58.146.76 Country: Canada Region: British Columbia City: Vancouver
sf16-scmcdn-sg.ibytedtos.com IP: 23.58.146.82 Country: Canada Region: British Columbia City: Vancouver
pitaya.tiktokv.com IP: 23.222.241.47 Country: United States of America Region: Texas City: Dallas
pitaya-task.tiktokv.com IP: 130.44.212.75 Country: United States of America Region: California City: Palo Alto
p16.tiktokcdn.com IP: 23.58.146.72 Country: Canada Region: British Columbia City: Vancouver
p16-webcast.tiktokcdn.com IP: 23.58.146.84 Country: Canada Region: British Columbia City: Vancouver
p16-tiktokcdn-com.akamaized.net IP: 23.58.146.81 Country: Canada Region: British Columbia City: Vancouver
p16-sg.tiktokcdn.com IP: 23.220.102.35 Country: United States of America Region: New Jersey City: Morristown
p16-sg-default.akamaized.net IP: 23.58.146.72 Country: Canada Region: British Columbia City: Vancouver
open-api.tiktok.com IP: 23.47.48.165 Country: United States of America Region: Texas City: Dallas
oec-api.tiktokv.com IP: 23.222.241.48 Country: United States of America Region: Texas City: Dallas
my-pac-script.invalid Not Available.
mon.tiktokv.com IP: 23.47.48.144 Country: United States of America Region: Texas City: Dallas
mon.isnssdk.com IP: 23.222.241.39 Country: United States of America Region: Texas City: Dallas
mon.byteoversea.com IP: 23.47.48.152 Country: United States of America Region: Texas City: Dallas
mon-va.tiktokv.com IP: 23.47.48.165 Country: United States of America Region: Texas City: Dallas
mon-va.byteoversea.com IP: 23.47.48.162 Country: United States of America Region: Texas City: Dallas
mon-sg.tiktokv.com IP: 23.222.241.48 Country: United States of America Region: Texas City: Dallas
m.tiktok.com IP: 23.47.48.168 Country: United States of America Region: Texas City: Dallas
log.tiktokv.com IP: 23.47.48.151 Country: United States of America Region: Texas City: Dallas
log-va.tiktokv.com IP: 23.222.241.42 Country: United States of America Region: Texas City: Dallas
libra-va.tiktokv.com IP: 23.222.241.42 Country: United States of America Region: Texas City: Dallas
libra-sg.tiktokv.com IP: 23.222.241.49 Country: United States of America Region: Texas City: Dallas
lf77-gecko-source.tiktokcdn.com IP: 156.146.38.3 Country: United States of America Region: Texas City: Dallas
lf19-gecko-source.tiktokcdn.com IP: 151.101.70.73 Country: United States of America Region: California City: San Francisco
lf19-gecko-source.tiktokcdn-us.com IP: 151.101.70.73 Country: United States of America Region: California City: San Francisco
lf16-insgame.tiktokcdn.com IP: 23.58.146.78 Country: Canada Region: British Columbia City: Vancouver
lf16-gecko-source.tiktokcdn.com IP: 23.58.146.83 Country: Canada Region: British Columbia City: Vancouver
lf16-gecko-source.tiktokcdn-us.com IP: 23.47.49.151 Country: United States of America Region: Texas City: Dallas
lf-main-gecko-source.tiktokcdn.com IP: 151.101.70.73 Country: United States of America Region: California City: San Francisco
jsb-va.byteoversea.com IP: 23.47.48.156 Country: United States of America Region: Texas City: Dallas
jsb-sg.byteoversea.com IP: 23.47.48.189 Country: United States of America Region: Texas City: Dallas
issuetracker.google.com IP: 142.250.72.78 Country: United States of America Region: California City: Mountain View
insgame-api-va.tiktokv.com IP: 23.222.241.58 Country: United States of America Region: Texas City: Dallas
insgame-api-sg.tiktokv.com IP: 23.222.241.50 Country: United States of America Region: Texas City: Dallas
insgame-api-i18n.tiktokv.com IP: 23.222.241.38 Country: United States of America Region: Texas City: Dallas
inapp.tiktokv.com IP: 23.222.241.58 Country: United States of America Region: Texas City: Dallas
inapp-va.tiktokv.com IP: 23.222.241.57 Country: United States of America Region: Texas City: Dallas
im-va.tiktokv.com IP: 23.47.48.146 Country: United States of America Region: Texas City: Dallas
i.sgsnssdk.com IP: 103.136.220.198 Country: Singapore Region: Singapore City: Singapore
i.isnssdk.com IP: 23.222.241.48 Country: United States of America Region: Texas City: Dallas
hotapi-va.tiktokv.com IP: 23.222.241.50 Country: United States of America Region: Texas City: Dallas
hotapi-sg.tiktokv.com IP: 23.222.241.51 Country: United States of America Region: Texas City: Dallas
go.onelink.me IP: 23.58.146.79 Country: Canada Region: British Columbia City: Vancouver
effecthouse.tiktok.com IP: 23.222.241.50 Country: United States of America Region: Texas City: Dallas Latitude: 32.783058 Longitude: -96.806671 View: Google Map
crbug.com IP: 216.239.32.29 Country: United States of America Region: California City: Mountain View
configure-platform.byteintl.com IP: 23.222.241.42 Country: United States of America Region: Texas City: Dallas
capcut-yt.onelink.me IP: 65.8.243.5 Country: United States of America Region: Washington City: Seattle
call-intercept.tiktok.com Not Available.
bytecast.byteintl.com IP: 23.222.241.53 Country: United States of America Region: Texas City: Dallas
bsync-va.tiktokv.com IP: 23.222.241.41 Country: United States of America Region: Texas City: Dallas
ars.appsflyer.com IP: 18.154.101.123 Country: United States of America Region: Washington City: Seattle
app-measurement.com IP: 142.250.72.78 Country: United States of America Region: California City: Mountain View
api21-normal-c-alisg.tiktokv.com IP: 151.101.70.73 Country: United States of America Region: California City: San Francisco
api21-core-c-alisg.tiktokv.com IP: 151.101.70.73 Country: United States of America Region: California City: San Francisco
api19-core-c-useast1a.tiktokv.com IP: 151.101.70.73 Country: United States of America Region: California City: San Francisco
api16-normal-c-alisg.tiktokv.com IP: 23.221.22.22 Country: United States of America Region: Texas City: Dallas
api16-normal-alisg.helo-api.com IP: 23.221.22.24 Country: United States of America Region: Texas City: Dallas
api16-core-c-useast1a.tiktokv.com IP: 23.221.22.5 Country: United States of America Region: Texas City: Dallas
api16-core-c-alisg.tiktokv.com IP: 23.221.22.16 Country: United States of America Region: Texas City: Dallas
api.twitter.com IP: 104.244.42.194 Country: United States of America Region: California City: San Francisco
api.tiktokv.com IP: 23.222.241.50 Country: United States of America Region: Texas City: Dallas
api.oston.io IP: 18.228.50.130 Country: Brazil Region: Sao Paulo City: Sao Paulo
api.keepon.media IP: 18.228.75.232 Country: Brazil Region: Sao Paulo City: Sao Paulo
api-va.tiktokv.com IP: 23.222.241.45 Country: United States of America Region: Texas City: Dallas
api-normal.tiktokv.com IP: 23.222.241.38 Country: United States of America Region: Texas City: Dallas
api-core.tiktokv.com IP: 23.222.241.48 Country: United States of America Region: Texas City: Dallas
android.googlesource.com IP: 64.233.182.82 Country: United States of America Region: California City: Mountain View
ads.tiktok.com IP: 23.222.241.55 Country: United States of America Region: Texas City: Dallas
access.line.me IP: 184.24.57.242 Country: United States of America Region: California City: Los Angeles
NETWORK DATA
Several attempts were made to intercept, decrypt, or MITM the data the app sends, and all failed, either due to resource issues due to the size of the APK, the fact that the app wouldn't run on emulators, anti-debugging measures, and the lack of rooted phone. For part two, these will be addressed by creating a very large virtual host instance to overcome the memory issues and procuring a rooted phone.
However, some information was available in logcat:
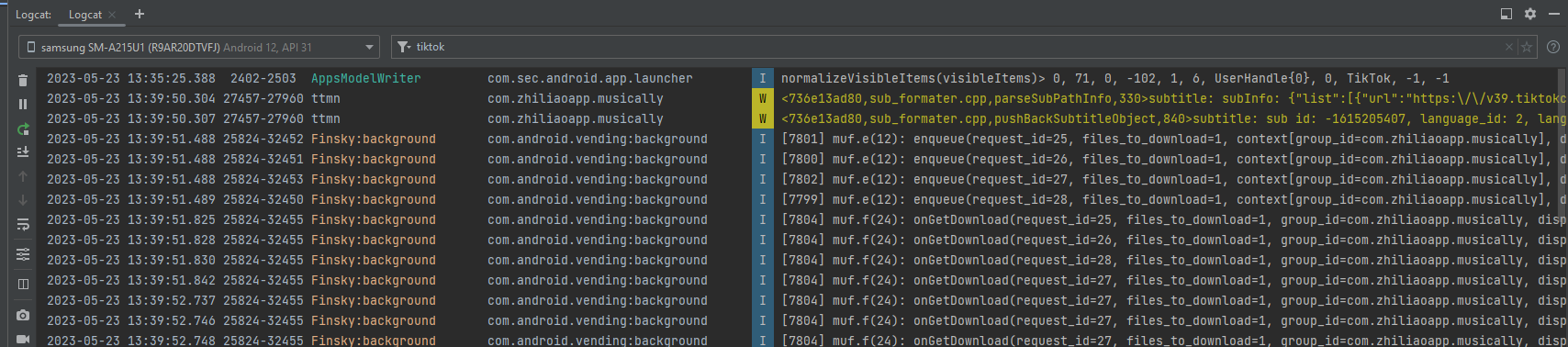
In this way the app was observed to send small amounts of encoded telemetry and other data to various tiktok affilated URLs. For example:
2023-05-23 13:39:50.304 27457-27960 ttmn com.zhiliaoapp.musically W <736e13ad80,sub_formater.cpp,parseSubPathInfo,330>subtitle: subInfo: {"list":[{"url":"https:\/\/v39.tiktokcdn-us.com\/2d6d6e0bd62de7b3924e10d4e367531b\/646d6711\/video\/tos\/useast5\/tos-useast5-v-0068-tx\/c8d5788e795544b0a6ccf68df77996b8\/?a=1233&ch=0&cr=3&dr=0&lr=all&cd=0%7C0%7C0%7C3&cv=1&br=13104&bt=6552&ds=4&ft=zagiWPMv2WkjVVwIwCs3usp3xbaySYxryLDCThbL&mime_type=video_mp4&qs=13&rc=amRucjk6ZmY2ajMzZzczNEBpamRucjk6ZmY2ajMzZzczNEBrcGszcjQwMGVgLS1kMS9zYSNrcGszcjQwMGVgLS1kMS9zcw%3D%3D&l=20230523192116F92FE36142624FA847CD&btag=e00000000","language_id":2,"for
There are also beacons and what likely amounts to log entries sent to various tiktok affiliated hosts over SSL on port 443:
[13:21:13.758][192.168.101.12:51128] server connect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.759][192.168.101.12:51132] server connect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.759][192.168.101.12:51130] server connect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.760][192.168.101.12:51126] server connect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.768][192.168.101.12:51134] server connect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.769][192.168.101.12:51122] server connect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.769][192.168.101.12:51138] server connect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.770][192.168.101.12:51120] server connect log-va.tiktokv.com:443 (184.28.29.61:443)
[13:21:13.772][192.168.101.12:51124] server connect log-va.tiktokv.com:443 (184.28.29.61:443)
[13:21:13.789][192.168.101.12:51136] server connect tiktokv.com:443 (23.48.12.90:443)
[13:21:13.808][192.168.101.12:51130] server disconnect api19-va.tiktokv.com:443 (151.101.70.73:443)
[13:21:13.808][192.168.101.12:51130] client disconnect
[13:21:13.808][192.168.101.12:51130] closing transports...
[13:21:13.809][192.168.101.12:51130] transports closed!
Here we can see the app failing to connect due to the MITM certificate I have installed in an attempt to intercept traffic. This is due to certificate pinning impelemented in the app. I have broken up, reformatted and decode the URL a bit to make it easier to see the telemetry data being sent:
2023-05-24 11:42:03.903 8084-10489 System.err com.zhiliaoapp.musically W X.F9S: :0|Exception in CronetUrlRequest: net::ERR_CERT_AUTHORITY_INVALID, ip=:0,
details={"has_upload":false,"is_pending":true,"load_flags":0,"load_state":3,"method":"GET","net_error":-202,"network_isolation_key":"null null","status":"FAILED","traffic_annotation":77012883,
"url":"https://webcast-va.tiktokv.com/webcast/setting/i18n/package/?locale=en
&cur_version=0
&webcast_sdk_version=2820
&webcast_language=en
&webcast_locale=en_US
&effect_sdk_version=0.0.0
¤t_network_quality_info=%7B%22
tcp_rtt%22%3A342%2C%22
quic_rtt%22%3A342%2C%22
http_rtt%22%3A342%2C%22
downstream_throughput_kbps%22%3A1400%2C%22
quic_send_loss_rate%22%3A-1%2C%22
quic_receive_loss_rate%22%3A-1%2C%22
net_effective_connection_type%22%3A3%2C%22
video_download_speed%22%3A1471%7D
=DECODED=
¤t_network_quality_info={"
tcp_rtt":342,
quic_rtt":342,
http_rtt":342,
downstream_throughput_kbps":1400,
quic_send_loss_rate":-1,
quic_receive_loss_rate":-1,
net_effective_connection_type":3,
video_download_speed":1471}
=DECODED=
&iid=7236479885107431210
&device_id=7236458780643493422
&ac=wifi
&channel=beta
&aid=1233
&app_name=musical_ly
&version_code=290116
&version_name=29.1.16
&device_platform=android
&ab_version=29.1.16
&ssmix=a
&device_type=SM-A215U1
&device_brand=samsung
&language=en
&os_api=31
&os_version=12
&openudid=1e2ff4cb705365f7
&manifest_version_code=2022901160
&resolution=7201437
&dpi=300
&update_version_code=2022901160
&_rticket=1684950118607
&app_type=normal
&sys_region=US
&timezone_name=America%2FDenver
&app_language=en
&ac2=wifi
&uoo=0&op_region=US
&timezone_offset=-25200
&build_number=29.1.16
&host_abi=arm64-v8a
®ion=US
&ts=1684950118
&cdid=4be0e7c2-44ac-4d67-81b3-80f7dcae8d9b","url_chain":["https://webcast-va.tiktokv.com/webcast/setting/i18n/package/?locale=en
&cur_version=0
&webcast_sdk_version=2820
&webcast_language=en&webcast_locale=en_US
&effect_sdk_version=0.0.0
¤t_network_quality_info=%7B%22tcp_rtt%22%3A342%2C%22quic_rtt%22%3A342%2C%22http_rtt%22%3A342%2C%22downstream_throughput_kbps%22%3A1400%2C%22quic_send_loss_rate%22%3A-1%2C%22quic_receive_loss_rate%22%3A-1%2C%22net_effective_connection_type%22%3A3%2C%22video_download_speed%22%3A1471%7D
&iid=7236479885107431210&device_id=7236458780643493422
&ac=wifi&channel=beta&aid=1233
&app_name=musical_ly
&version_code=290116
&version_name=29.1.16
&device_platform=android
&ab_version=29.1.16
&ssmix=a
&device_type=SM-A215U1
&device_brand=samsung
&language=en
&os_api=31
&os_version=12
&openudid=1e2ff4cb705365f7
&manifest_version_code=2022901160
&resolution=7201437
&dpi=300
&update_version_code=2022901160
&_rticket=1684950118607&app_type=normal
&sys_region=US
&timezone_name=America%2FDenver
&app_language=en
&ac2=wifi
&uoo=0
&op_region=US&timezone_offset=-25200
&build_number=29.1.16
&host_abi=arm64-v8a
®ion=US
&ts=1684950118
&cdid=4be0e7c2-44ac-4d67-81b3-80f7dcae8d9b","https://webcast16-normal-useast5.us.tiktokv.com/webcast/setting/i18n/package/?locale=en
&cur_version=0
&webcast_sdk_version=2820
&webcast_language=en
&webcast_locale=en_US
&effect_sdk_version=0.0.0
¤t_network_quality_info=%7B%22tcp_rtt%22%3A342%2C%22quic_rtt%22%3A342%2C%22http_rtt%22%3A342%2C%22downstream_throughput_kbps%22%3A1400%2C%22quic_send_loss_rate%22%3A-1%2C%22quic_receive_loss_rate%22%3A-1%2C%22net_effective_connection_type%22%3A3%2C%22video_download_speed%22%3A1471%7D
&iid=7236479885107431210
&device_id=7236458780643493422
&ac=wifi
&channel=beta
&aid=1233
&app_name=musical_ly
&version_code=290116
&version_name=29.1.16
&device_platform=android
&ab_version=29.1.16
&ssmix=a
&device_type=SM-A215U1
&device_brand=samsung
&language=en
&os_api=31
&os_version=12
&openudid=1e2ff4cb705365f7
&manifest_version_code=2022901160
&resolution=720*1437
&dpi=300
&update_version_code=2022901160
&_rticket=1684950118607
&app_type=normal
&sys_region=US
&timezone_name=America%2FDenver
&app_language=en
&ac2=wifi
&uoo=0
&op_region=US
&timezone_offset=-25200
&build_number=29.1.16
&host_abi=arm64-v8a
®ion=US
&ts=1684950118
&cdid=4be0e7c2-44ac-4d67-81b3-80f7dcae8d9b"]}, attempts= , dns=-1, connect=-1, ssl=-1, send=-1, proxy=-1, wait=-1, receive=-1, total=-1, reused=0, cached=0, response_content_len=0, total_bytes=0, is_proxy=0, QuicStreamError=0, QuicCloseSource=0, H2ProtocolError=-1, RFC7540Error=-1, ErrorCode=11, InternalErrorCode=-202, Retryable=false, ErrorCode=11, InternalErrorCode=-202, Retryable=false
So you can see it sends everything from where you are located, what type of network you are using, network quality, the resolution of your phone, etc.
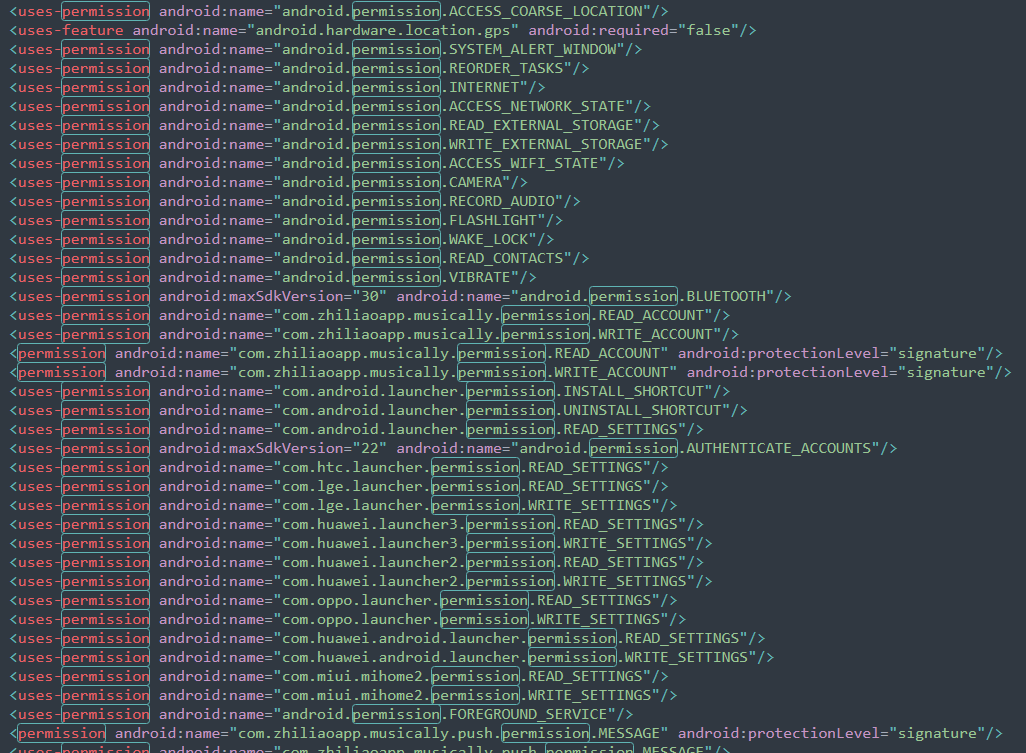
PERMISSIONS
The app requests several permissions, a number of which can be dangerous from a privacy perspective:
android.permission.ACCESS_COARSE_LOCATION | coarse (network-based) location
android.permission.AUTHENTICATE_ACCOUNTS | act as an account authenticator
android.permission.CAMERA | take pictures and videos
android.permission.READ_CONTACTS | read contact data
android.permission.READ_EXTERNAL_STORAGE | read external storage contents
android.permission.RECORD_AUDIO | record audio
android.permission.SYSTEM_ALERT_WINDOW | display system-level alerts
android.permission.WRITE_EXTERNAL_STORAGE | read/modify/delete external storage contents
And the other permissions it uses, several of which appear to be more hardware specific:
com.google.android.c2dm.permission.RECEIVE
android.permission.BLUETOOTH_CONNECT
com.amazon.device.messaging.permission.RECEIVE
com.android.launcher.permission.INSTALL_SHORTCUT
com.android.launcher.permission.READ_SETTINGS
com.android.launcher.permission.UNINSTALL_SHORTCUT
com.android.vending.BILLING
com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE
com.huawei.launcher2.permission.READ_SETTINGS
com.huawei.launcher2.permission.WRITE_SETTINGS
com.huawei.launcher3.permission.READ_SETTINGS
com.huawei.launcher3.permission.WRITE_SETTINGS
com.lge.launcher.permission.READ_SETTINGS
com.lge.launcher.permission.WRITE_SETTINGS
com.miui.mihome2.permission.READ_SETTINGS
com.miui.mihome2.permission.WRITE_SETTINGS
com.orange.update.permission.READ_ATTRIBUTION
com.samsung.android.mapsagent.permission.READ_APP_INFO
com.tiktok.preload.permission.IDENTIFY
com.huawei.launcher2.permission.WRITE_SETTINGS
com.huawei.launcher3.permission.READ_SETTINGS
com.huawei.launcher3.permission.WRITE_SETTINGS
com.lge.launcher.permission.READ_SETTINGS
com.lge.launcher.permission.WRITE_SETTINGS
com.miui.mihome2.permission.READ_SETTINGS
com.miui.mihome2.permission.WRITE_SETTINGS
com.orange.update.permission.READ_ATTRIBUTION
com.samsung.android.mapsagent.permission.READ_APP_INFO
com.tiktok.preload.permission.IDENTIFY
Some of the permissions can be seen in this snippet of the decoded AndroidManifest.xml file:
POTENTIAL SECURITY ISSUES
There are several potential security issues in the app. Some attempts were made to verify these, but some of them could be false positives:
1.) Base config is insecurely configured to permit clear text traffic to all domains.
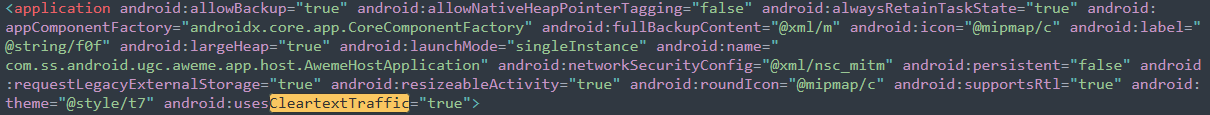
This is probably just for backup purposes as the bulk of the traffic observed was SSL encrypted. However there can be sensitive information transmitted in backups. It's unclear at this time how this is used.
2.) Base config is configured to bypass certificate pinning.
Some scanners indicate that this is the case, but I wasn't able to find evidence in the code for this. In some of the smali files there are indicators that certificate pinning is enforced.
smali_classes11/X/Qh1.1.smali: invoke-virtual {v1, v0}, LX/FRC;->certificatePinner(LX/FRI;)LX/FRC;smali_classes6/X/FRC.smali:.field public certificatePinner:LX/FRI;smali_classes6/X/FRC.smali: iput-object v0, p0, LX/FRC;->certificatePinner:LX/FRI;smali_classes6/X/FRC.smali:.method public final certificatePinner(LX/FRI;)LX/FRC;smali_classes6/X/FRC.smali: iput-object p1, p0, LX/FRC;->certificatePinner:LX/FRI;smali_classes6/X/FRC.smali: const-string v0, "certificatePinner == null"smali_classes6/X/FRD.smali: iget-object v3, p1, LX/FRC;->certificatePinner:LX/FRI;
3.) The App uses the encryption mode CBC with PKCS5/PKCS7 padding. This configuration is vulnerable to padding oracle attacks.
4.) Weak Encryption algorithm used.
5.) Remote WebView debugging is enabled.
6.) Application vulnerable to Janus Vulnerability.
7.) App uses SQLite Database and execute raw SQL query. Untrusted user input in raw SQL queries can cause SQL Injection. Also sensitive information should be encrypted and written to the database.
8.) Insecure WebView Implementation. Execution of user controlled code in WebView is a critical Security Hole.
9.) The App uses an insecure Random Number Generator. (This one is interesting, for later follow up.)
10.) Files may contain hardcoded sensitive information like usernames, passwords, keys etc.
11.) Application contains Privacy Trackers
CODE ANALYSIS
Several items of code within the app were examined. In the following section various API calls, Java files, and components of the app are examined for potentially negative behavior from a privacy standpoint:
Get Cell Location
ApiHookConfig.java
This is an interesting file. This indicates that it can hook, intercept and examine all these API calls. This covers most aspects of the phone that would be of interest from collecting phone characteristics such as the IMEI, listing installed packages, taking data from the clipboard, collecting seen WIFI networks, using the camera and microphone, etc.
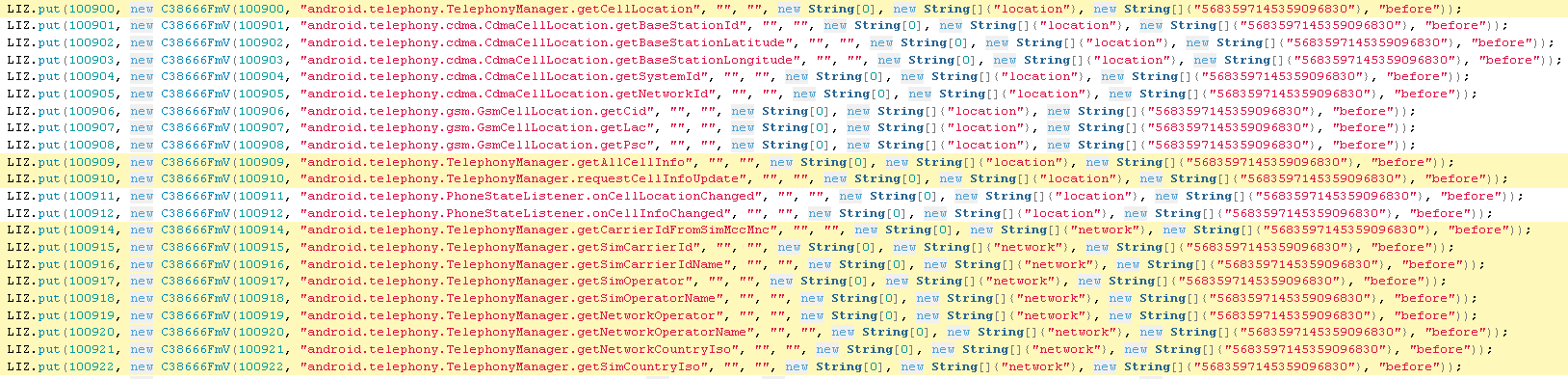
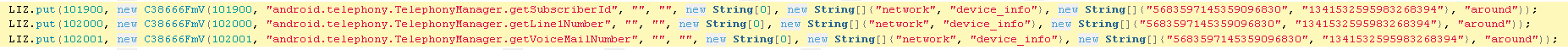
GET CELL NETWORK INFO
CellUtil.java
This code has the capability to gather information about the cell network the phone is connected to:
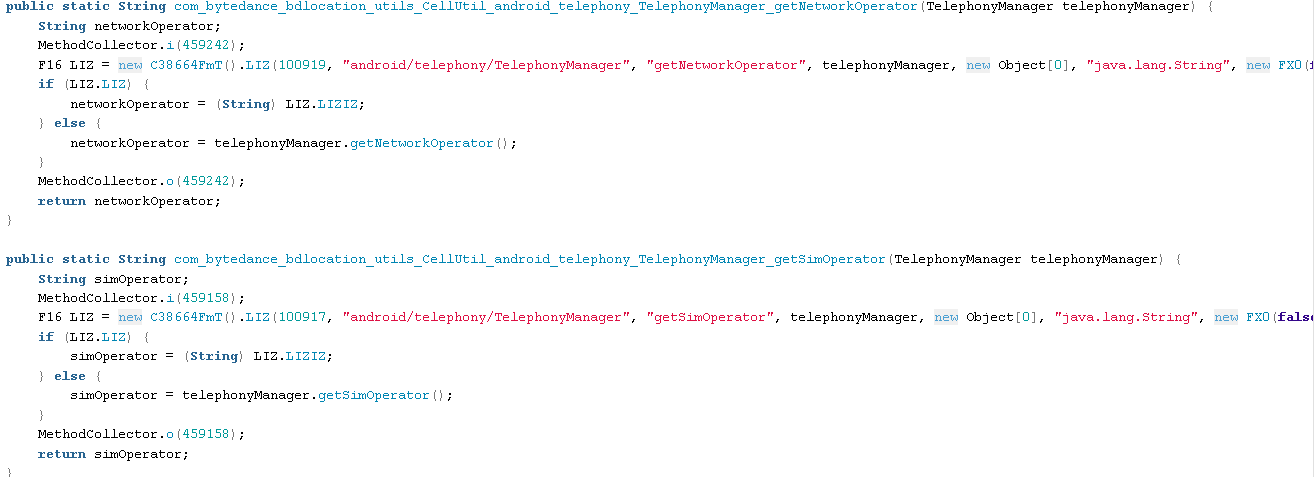
Get WiFi Details
There are several files which gather information about the current wifi connection. This is one example:
C33929Dp0.java
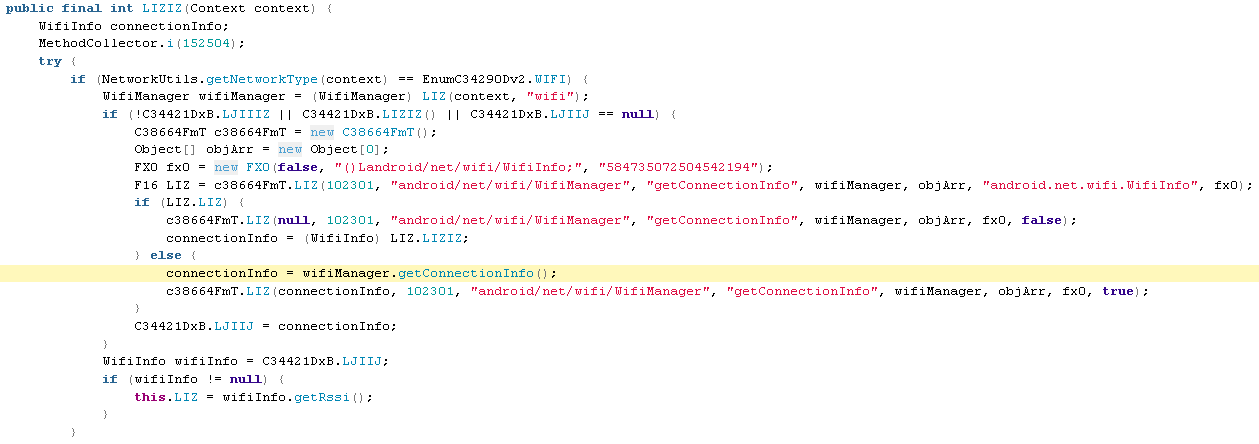
GPS Location
There are several files which gather information about the GPS location of the phone. These are a couple of examples:
C02U.java
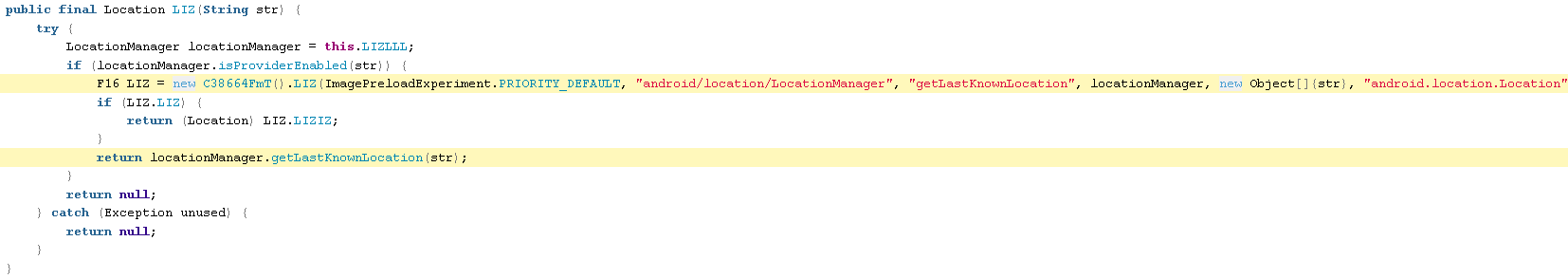
C60081Our.java
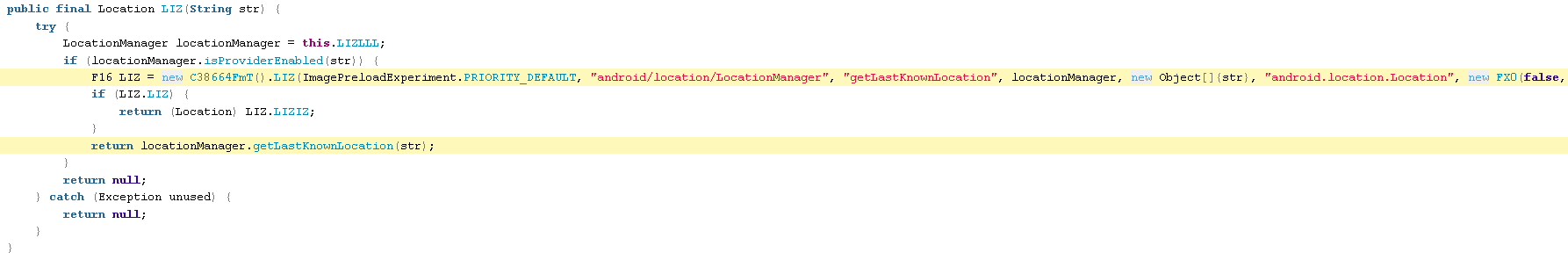
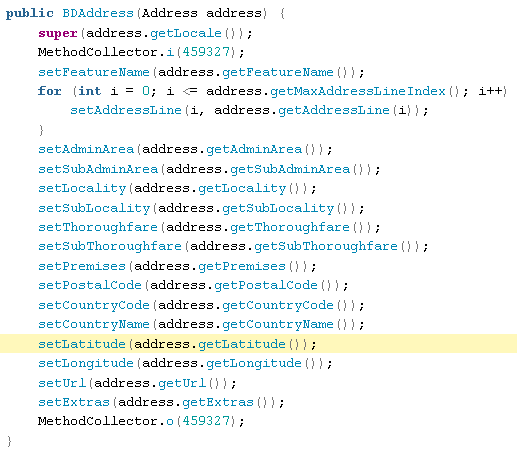
BDAddress.java
SEND RECORDED AUDIO OVER HTTP
There is some code that appears to be for sending recorded audio back to TikTokServers over HTTP. This is to be expected if the user is recording and posting content. This could be related to the videos a user records for TikTok or it could be other recorded audio.
WebRtcAudioFile.java
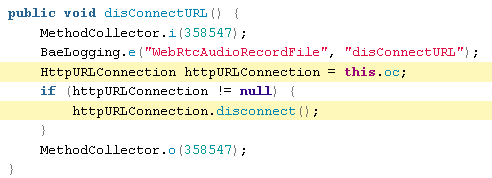
There is some other code that seems to indicate it sends the audio file back to ByteDance:
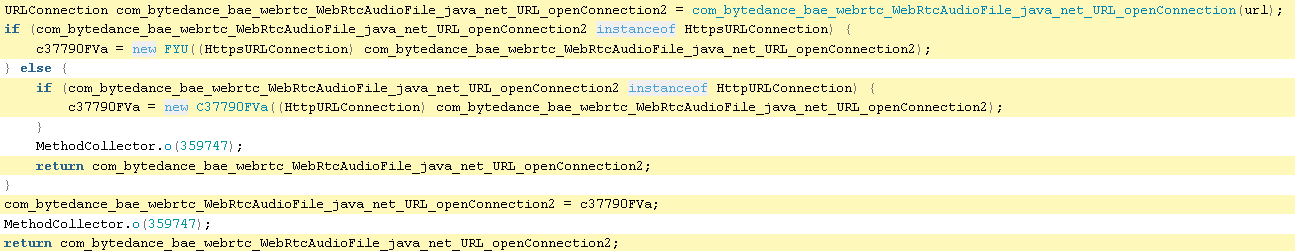
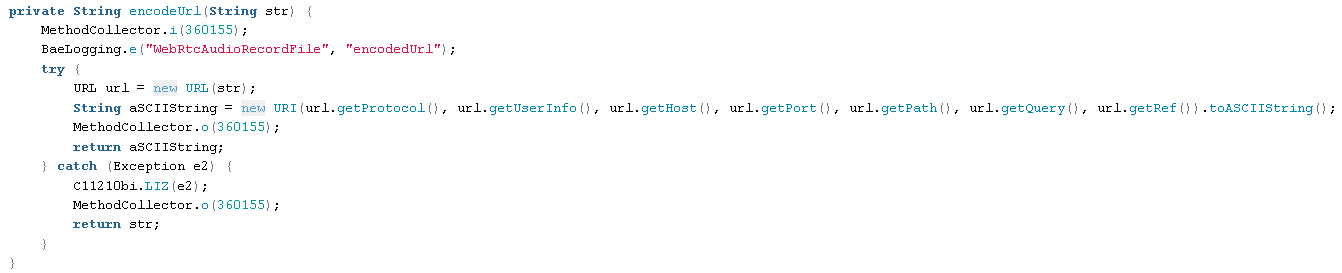
Additionally, it includes some telemetry data about the phone along with the audio file:
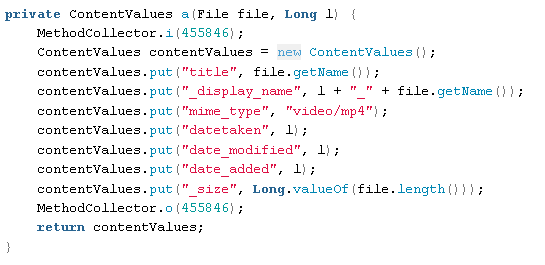
VIDEO HANDLING
This is likely related to the files the user records for TikTok but shows that it has video handling capabilities as expected:
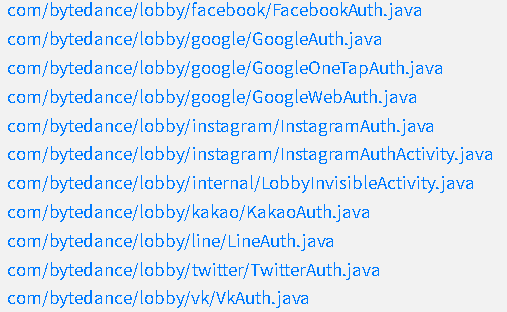
EXTERNAL AUTHENTICATION
Some examples of files associated with external service authentication:
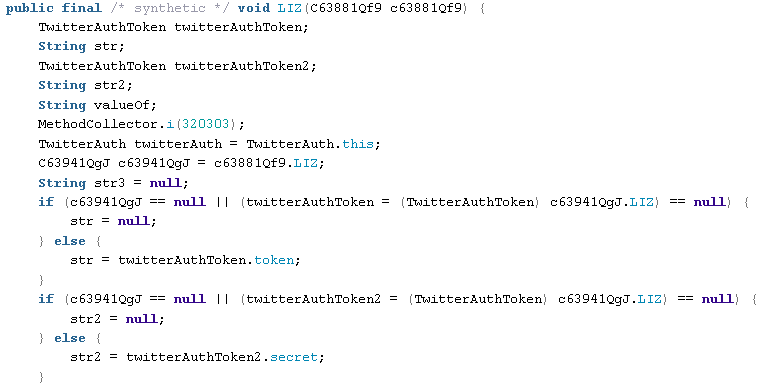
One interesting example is the manipulation and use of the Twitter account including username and authentication token:
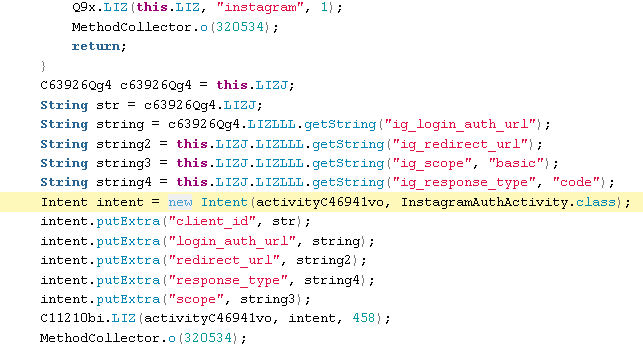
Another example exists in the Instagram code:
InstagramAuth.java
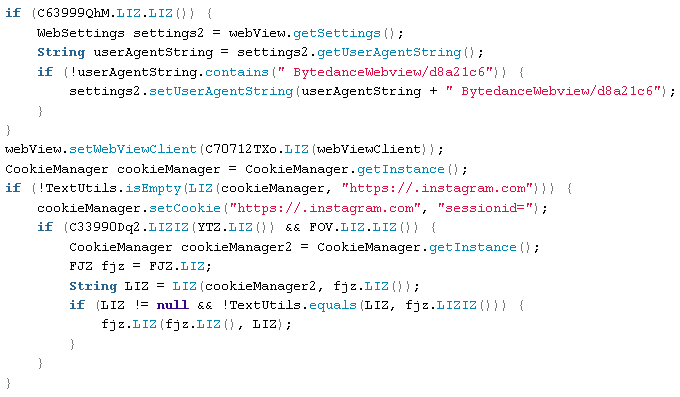
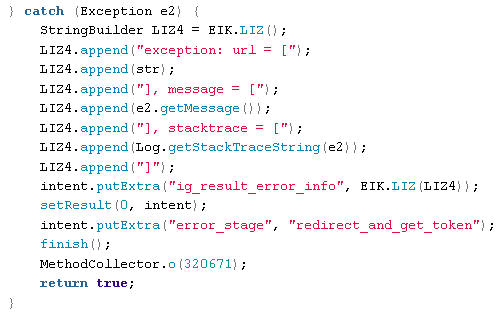
This code also handles Instagram cookies and collects stack traces on exceptions related to Instagram authentication:
InstagramAuthActivity.java
HARDWARE INFORMATION COLLECTION
Hardware.java
This code collects some basic information about the hardware including CPU information, battery status, disk space, screen resolution, operating system version, total amount of memory, etc. Of note is some code that looks at the accelerometer as well as the devices rotation:
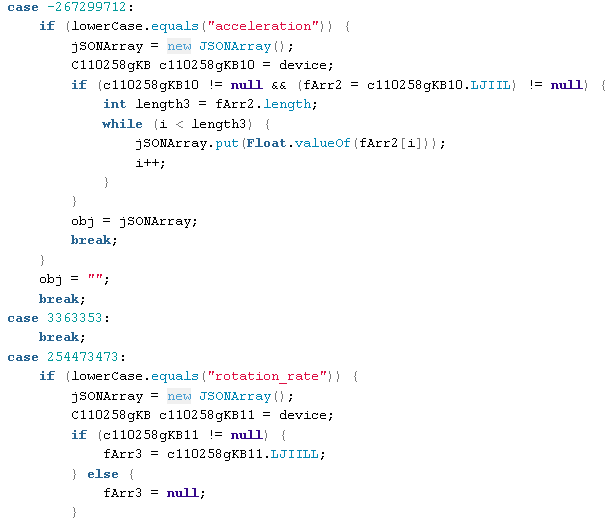
NETWORK MANIPULATION
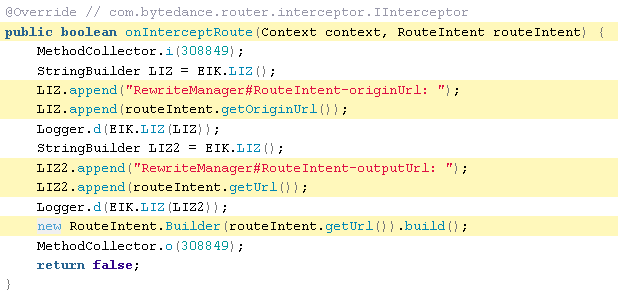
RewriteManager.java
The following snippet of code is from a file which appears to be for re-writing URLs the phone communicates with in certain circumstances:
COLLECT NETWORK INFORMATION
NetworkUtil.java
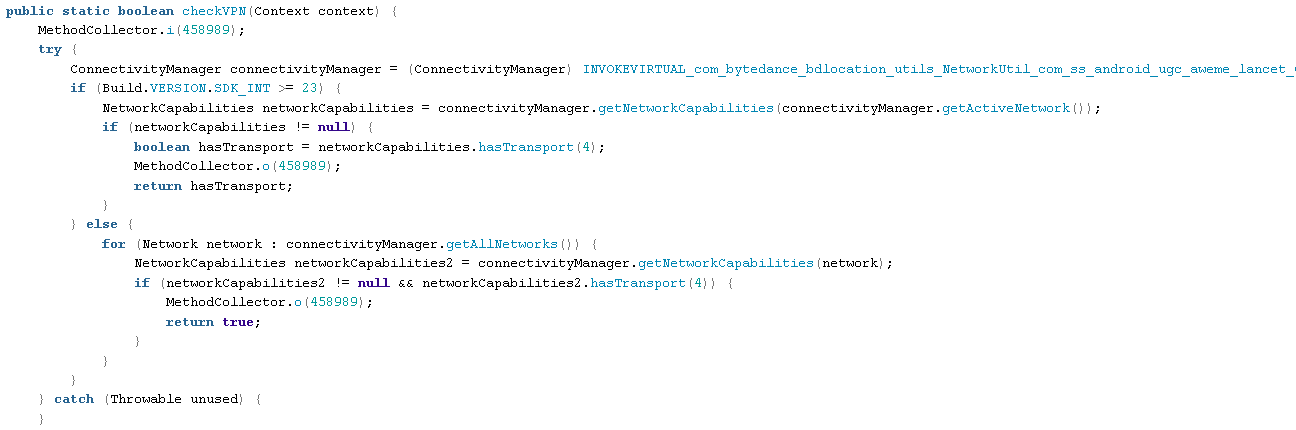
These are interesting because while it is important to understand the phone's network configuration for app operability, from a censorship perspective it is useful to know if someone is attempting to subvert network controls. Also this type of functionality can be used to make the analysis we are doing here more difficult.
Identify if device is on a VPN:
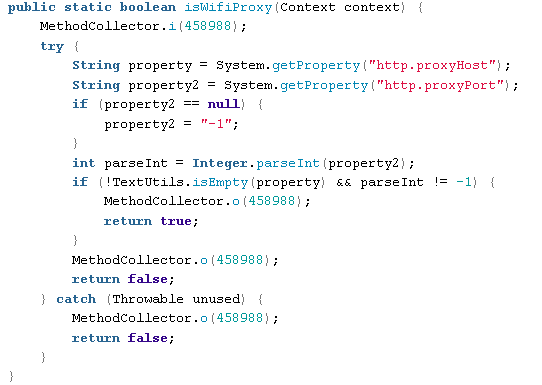
Identify if device is using a web proxy:
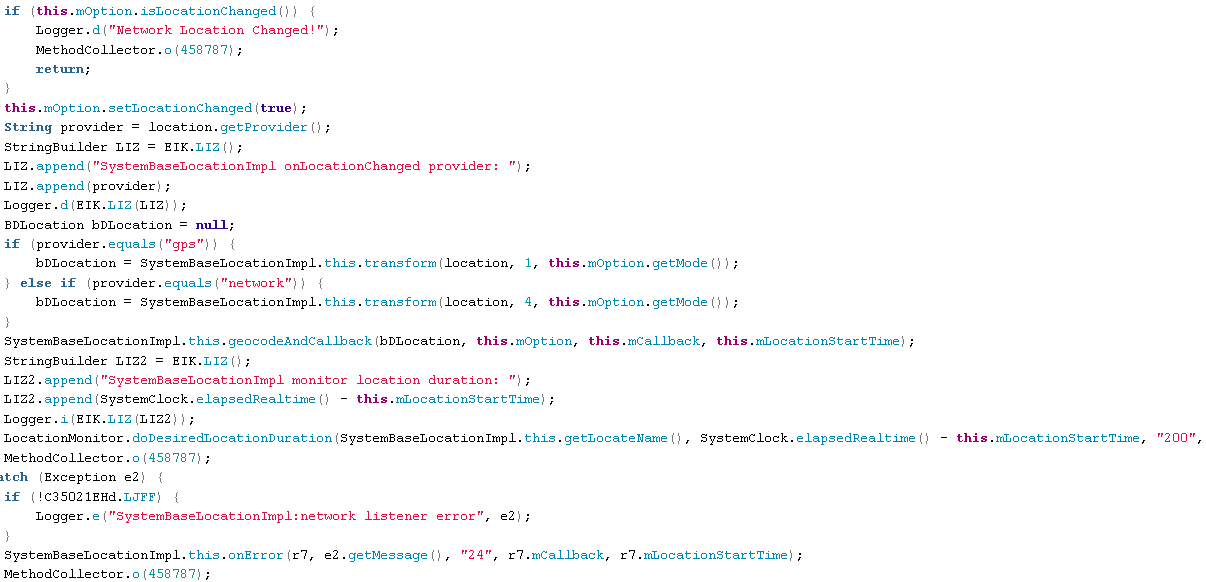
Identify phones location from network data and if the phone has moved:
SystemBaseLocationImpl.java
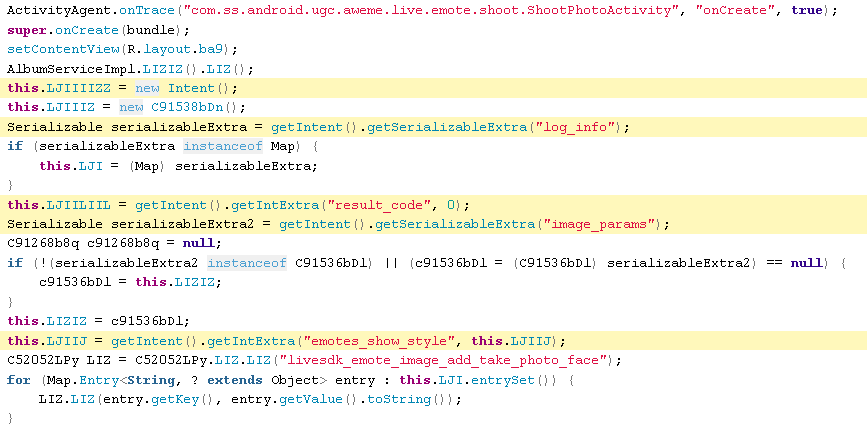
CAMERA MANIPULATION
This is to be expected since this app is for recording and posting videos. No evidence that this was being used in a nefarious way was observed.
ShootPhotoActivity.java
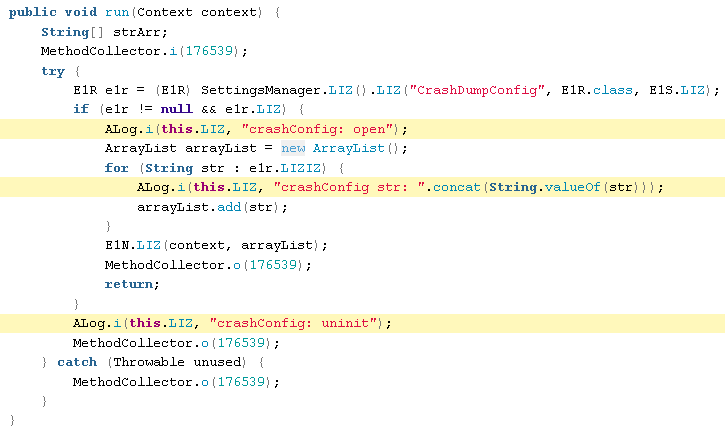
CRASH DUMPS
There is some code that appears to be able to generate and handle a crash dump. This is useful for a variety of reasons, for quality control and debugging, as well as for collecting sensitive information.
CrashDumpTask.java
Crash dumps are interesting because they can contain raw, cleartext, sensitive data from memory.
TRACKING
The app has four trackers. The one that really matters is AppsFlyer.
AppsFlyer tracks users across multiple devices, collects their behavior, as well as provides identity attribution services. According to VentureBeat, AppsFlyer leverages metadata from 98% of the world's mobile devices. I have not heard of this service before butt it merits a deeper look.
The other trackers are just common Facebook / Google trackers.
TODO
For Part 2 we will test on a rooted phone, build a 192 GB memory virtual machine for APK manipulation, and run down some of the interesting findings from Part 1.
If there is interest, let me know, and we can do a comparison between TikTok and other similar social media apps. I suspect they will be very similar.
Finally, I will do a post digging into the methodologies in detail such as de-cert pinning, debugging the app, etc.
Thanks for reading!
A.

