Unusual Spear Phish

We received an email that was a little strange and so I decided to check it out.
Email Contents
The contents of the email were as follows:
________________________________________________________
Dear Suppliers,
We attempted to contact a representative from your company several times over the last few weeks, but were unsuccessful. A request for quotation (RFQ) with the number CFTC-494 has been sent to your company. The Commodity Futures Trading Commission (CFTC) is looking to purchase the items listed in the attached quote.
We kindly request that you provide your best pricing with FOB destination, along with any applicable discount for bulk orders.
Please ensure your quote includes the following information:
* Itemized list of the computer peripherals, including quantity and unit price
* Total cost, including any applicable taxes and shipping fees
* Any applicable discounts or promotions
* Warranty, expected delivery time and shipping details
Please note that any responses received after the deadline, unless received via email, will not be accepted. Suppliers/Vendors are encouraged to take their time in submitting their RFQ pricing documents on time.
Your prompt attention to this matter is greatly appreciated.
Thank you and regards,
----
David Gillers
Senior Procurement Executive
Acquisitions & Business Services
Commodity Futures Trading Commission
1155 21st Street, NW | Washington, DC 20581
Phone: (202) 697-9509
This e-mail is confidential, intended only for the named recipient(s) above and contains information that is privileged. If you have received this e-mail in error, please notify us immediately by using the reply facility on your e-mail system. Nothing in this communication is intended to operate as an electronic signature under applicable law.
________________________________________________________
There is an embedded image in the email pointing to:<img alt="" src="https://i.i mgur.com/oh4hYKW.png" style="width: 199px; height: 130px;">
To download it with wget you have to provide a user-agent string otherwise imgur gives an error. I included the server response to see if there was anything strange. There is an ETag, but I doubt the sender has any control over that or imgur.
wget --server-response --user-agent='Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36' https://i.imgur.com/oh4hYKW.png--2024-06-12 23:45:21-- https://i.imgur.com/oh4hYKW.pngResolving i.imgur.com (i.imgur.com)... 146.75.104.193Connecting to i.imgur.com (i.imgur.com)|146.75.104.193|:443... connected.HTTP request sent, awaiting response... HTTP/1.1 200 OK Connection: keep-alive Content-Length: 19099 Content-Type: image/png Last-Modified: Thu, 06 Jun 2024 15:18:33 GMT ETag: "dee08b3044b9cd1f1590d07846a4a452" x-amz-server-side-encryption: AES256 X-Amz-Cf-Pop: MIA3-P1 X-Amz-Cf-Id: IyN67XAfcFO8bdjGvjFXGzYt08Aoz_s-3-FjKlcx4bivgIwjgJNIkQ== cache-control: public, max-age=31536000 Accept-Ranges: bytes Age: 281043 Date: Wed, 12 Jun 2024 23:45:21 GMT X-Served-By: cache-iad-kcgs7200041-IAD, cache-dfw-kdfw8210080-DFW X-Cache: Miss from cloudfront, HIT, HIT X-Cache-Hits: 5, 0 X-Timer: S1718235922.951180,VS0,VE1 Strict-Transport-Security: max-age=300 Access-Control-Allow-Methods: GET, OPTIONS Access-Control-Allow-Origin: * Server: cat factory 1.0 X-Content-Type-Options: nosniffLength: 19099 (19K) [image/png]Saving to: ‘oh4hYKW.png’
The EXIF information for the file is:ExifTool Version Number : 11.88File Name : oh4hYKW.pngDirectory : .File Size : 19 kBFile Modification Date/Time : 2024:06:06 15:18:33+00:00File Access Date/Time : 2024:06:12 23:43:19+00:00File Inode Change Date/Time : 2024:06:12 23:43:13+00:00File Permissions : rw-r--r--File Type : PNGFile Type Extension : pngMIME Type : image/pngImage Width : 198Image Height : 164Bit Depth : 8Color Type : RGBCompression : Deflate/InflateFilter : AdaptiveInterlace : NoninterlacedImage Size : 198x164Megapixels : 0.032
So we can see it was created relatively recently.
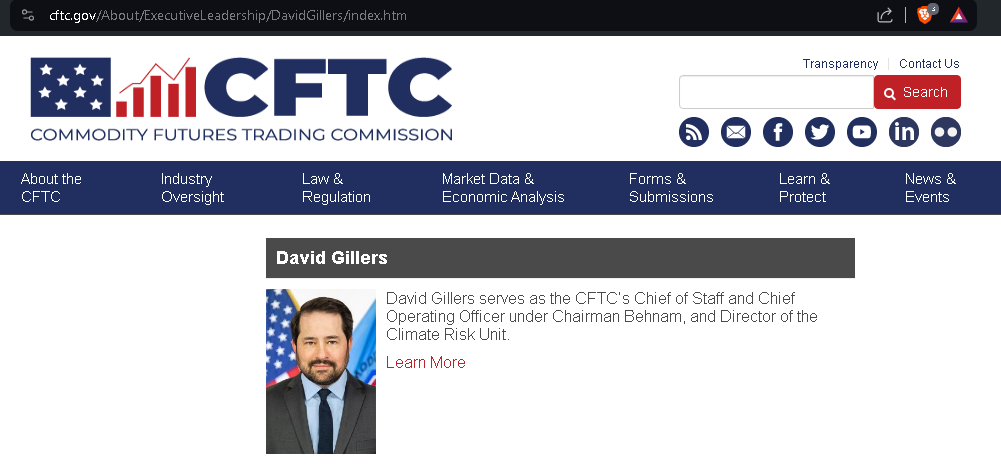
The CFTC is a real organization and David Gillers is a member of that organization, however, he isn't a Senior Procurement Executive, he is the Chief of Staff and COO:
Lets look at the message headers.
Message Headers
Message headers
Close
Return-Path: <admin@nccofl.org>
X-Original-To: *************************
Delivered-To: *************************
Received: from hosting.dataspace.com.np (hosting.dataspace.com.np [103.243.100.13])
(using TLSv1.2 with cipher ECDHE-RSA-AES256-GCM-SHA384 (256/256 bits)) (No client
certificate requested) by ************** (Postfix) with ESMTPS id
4Vzw2V1wMQz9vPJY for <*************************>; Wed, 12 Jun 2024 19:04:33 +0000 (UTC)
Received: from nccofl_admin by hosting.dataspace.com.np with local (Exim 4.97.1)
(envelope-from <admin@nccofl.org>) id 1sHTGg-0000000073Z-2YjN for
*************************; Thu, 13 Jun 2024 00:49:22 +0545
Authentication-Results: **************; dmarc=none (p=none dis=none)
header.from=cftcc.gov
Authentication-Results: **************; spf=pass smtp.mailfrom=nccofl.org
Authentication-Results: **************; arc=none smtp.remote-ip=103.243.100.13
Authentication-Results: **************; dkim=none
To: *************************
Subject: Computer Peripheral Quote #: CFTC-495
X-Php-Originating-Script: 1017:.alexus.php
From: David Gillers <david.gillers@cftcc.gov>
Mime-Version: 1.0
Content-Type: text/html
Reply-To: David Gillers <david.gillers@cftccgov.org>
Message-Id: <E1sHTGg-0000000073Z-2YjN@hosting.dataspace.com.np>
Date: Thu, 13 Jun 2024 00:49:22 +0545
X-Pm-Spam: 0yezJI6YSpyJec91ztFGcjIxoJyLCvXBZcQniisnOkQZFNfRVijANOslxzJCL2Yy9ogZT2C4MNED0s0lIkIPJVTR1J01XTVUfSVkV0UPlI6TiuzMWN0VsSZkI0Tf1hDRVTVNRXJ0B2U0UCN6IBdWzICJLRFUEfJVRlRPJ9ETVGUZSRJVFfRlTERN9lOQU6yIUWAzus0lMkIUhxfTUBU1SRV0fM50TVWy8I6NCuzAWN0VsUhkIUTfxVTTUH0FURIS6dBzWCLNJdJU0GF9RU9kNU10XVQI9FERUiVIROslwiwSXkUWN9JRFWl9TQxUJUlERVWD9JURVJUZSRRUfPxkQ0QFtI6RCszAWIEjwy4yMDNuMAwMTzjELIxGplR3
<--SNIP--->
Y6I4wMC3DAMMUDwwADMTMxMMwMT5jEMLJCtslWY2XhNVndG53JbX12vsVGZjIioFpbWhGNbd5Cji12bWal59mZFlW5adVHuuQWZjMyAAyNDujEMYt2wsICdmIh1xfaW02FYZdWvflncmbtFI6ZSQlVIRFEUiMVRCLtJlsYWh2NXdVGn5J3b3XyBIib2ujAONAzz3UTMDM3Ak0Nj0jQMNwCiz9FcGctFowIjyjALMQj51YzMTMzEc1Nj0TkNMwyiuVnc2Xh5UibWuiJOZcXtuV2cGZyV19IniSwfcJ3p6ICZjI2YlmNj2TQMY EW3kN2NTOwUZjNGlTVNYJy9fQ==
X-Attached: CFTC-4295.pdf
X-Pm-Origin: external
X-Pm-Transfer-Encryption: TLSv1.2 with cipher ECDHE-RSA-AES256-GCM-SHA384 (256/256 bits)
X-Pm-Content-Encryption: on-delivery
X-Pm-Spamscore: 5
X-Pm-Spam-Action: inbox
A few things stand out:
| Return-Path: |
admin@nccofl.org |
| Received: from |
hosting.dataspace.com.np 103.243.100.13] |
| Reply-To: David Gillers |
david.gillers@cftccgov.org Notice that its now a .org |
Domain & IP Analysis
The IP for nccofl.org is 103.243.101.13.
Registrar: PDR Ltd. d/b/a PublicDomainRegistry.com
Every other detail of the domain shows: REDACTED FOR PRIVACY
The IP has the following information:
inetnum: 103.243.100.0 - 103.243.101.255
netname: DATASPACEPVTLTD-NP
descr: Dataspace Pvt. Ltd.
country: NP
org: ORG-DPL33-AP
admin-c: DPLA23-AP
tech-c: DPLA23-AP
abuse-c: AD1277-AP
status: ASSIGNED PORTABLE
mnt-by: APNIC-HM
mnt-routes: MAINT-DATASPACEPVTLTD-NP
mnt-irt: IRT-DATASPACEPVTLTD-NP
last-modified: 2023-07-25T04:04:41Z
source: APNIC
irt: IRT-DATASPACEPVTLTD-NP
address: Putalisadak-28, Kathmandu Bagmati 44600
admin-c: DPLA23-AP
tech-c: DPLA23-AP
organisation: ORG-DPL33-AP
org-name: Dataspace Pvt. Ltd.
org-type: LIR
country: NP
address: Putalisadak-28
phone: +977-1-5369718
e-mail: ds@ds.com.np
The IP is registered in NEPAL.
The IP for cftccgov.org is 84.32.84.32.
It appears to be located in:
Ground Floor, 4 Victoria Square, St Albans, Hertfordshire, AL1 3TF, UK
File Analysis
| FILE TYPE: |
CFTC-4295.pdf: PDF document, version 1.7, 1 pages (zip deflate encoded) |
| FILE SIZE: |
232K |
| MD5SUM: |
85609e747dae737adcb6b20fca1a2221 |
| VIRUSTOTAL: |
No detections |
| PDF ANALYSIS: |
Incremental update: 1: objects= 32 length= 234463 difference= 234463 << /Contents 12 0 R /Group << /CS /DeviceRGB /S /Transparency /Type /Group >> /MediaBox [ 0 0 612 792 ] /Parent 13 0 R /Resources << /ExtGState << /GS10 6 0 R /GS6 5 0 R >> /Font << /F1 7 0 R /F2 8 0 R /F3 9 0 R /F4 10 0 R /F5 11 0 R >> /ProcSet [ /PDF /Text /ImageB /ImageC /ImageI ] /XObject << /Image11 3 0 R /Image13 4 0 R /Image4 2 0 R >> >> /Tabs /S /Type /Page >>
|
I can't really find any evidence of an exploit or other type of attack within the PDF so I decided to look at it in a controlled system and see what the contents were:

Looks fairly official, but its requesting my contact info.
I analyzed some of the meta data from the PDF and found:
<?xpacket begin='' id='W5M0MpCehiHzreSzNTczkc9d'?><?adobe-xap-filters esc="CRLF"?><x:xmpmeta xmlns:x='adobe:ns:meta/' x:xmptk='3.1-702'><rdf:RDF xmlns:rdf='http://www.w3.org/1999/02/22-rdf-syntax-ns#'><rdf:Description rdf:about='23B7679B-EEDE-57C7-267A-95E8A8FE1EFC' xmlns:pdf='http://ns.adobe.com/pdf/1.3/'><pdf:Keywords>www.Neevia.com, Document Converter Pro, Convert to PDF or Image in batches!</pdf:Keywords><pdf:Producer>Neevia Document Converter Pro v7.5.0.241 (http://neevia.com)</pdf:Producer></rdf:Description><rdf:Description rdf:about='23B7679B-EEDE-57C7-267A-95E8A8FE1EFC' xmlns:xmp='http://ns.adobe.com/xap/1.0/'><xmp:ModifyDate>2024-06-10T05:12:02-04:00</xmp:ModifyDate><xmp:CreateDate>2024-06-10T05:12:02-04:00</xmp:CreateDate><xmp:MetadataDate>2024-06-10T05:12:02-04:00</xmp:MetadataDate><xmp:CreatorTool>Microsoft Word 2016</xmp:CreatorTool></rdf:Description><rdf:Description rdf:about='23B7679B-EEDE-57C7-267A-95E8A8FE1EFC' xmlns:dc='http://purl.org/dc/elements/1.1/'><dc:format>application/pdf</dc:format><dc:description><rdf:Alt><rdf:li xml:lang='x-default'></rdf:li></rdf:Alt></dc:description><dc:creator><rdf:Seq><rdf:li>Windows User</rdf:li></rdf:Seq></dc:creator><dc:title><rdf:Alt><rdf:li xml:lang='x-default'></rdf:li></rdf:Alt></dc:title></rdf:Description><rdf:Description rdf:about='23B7679B-EEDE-57C7-267A-95E8A8FE1EFC' xmlns:xmpMM='http://ns.adobe.com/xap/1.0/mm/'><xmpMM:DocumentID>uuid:008A1793-EDB4-5D17-C264-47F9AB37C26F</xmpMM:DocumentID><xmpMM:InstanceID>uuid:23B7679B-EEDE-57C7-267A-95E8A8FE1EFC</xmpMM:InstanceID></rdf:Description>
Neevia Document Converter Pro is a software product that dynamically converts Microsoft Office 2007/2010/2013/2016/2019/365, WordPerfect, HTML, AutoCAD DWG/DWF, EML, MSG, PostScript and many other document types to PDF, PDF/A, PostScript, JPEG, TIFF, PNG, PCX, BMP. To me, this indicates that they created the document in Word and then used Neevia to convert it to PDF, which is a little strange since Word can already export to PDF, but maybe they wanted to control the meta data.
Essentially, it looks like the trick is to get me to fill out the PDF and reply to the fake gov address. I don't know if this is just for data collection, or to establish contact, or what the purpose is.
I checked our various logs and servers to see if that IP, or one similar, had contacted any of our systems but no luck.
In any case, I'm not sure we are the right people to send spear phishes to, but I appreciate it as it gives me more content for my blog and sometimes I get novel techniques I can reuse.
Thanks for reading.
A.

