What I am Doing - Fun With Signals

A friend of mine and I both ordered flipperzero devices recently. His seems to have been seized by customs and mine showed up a couple of days ago so I decided to setup a basic test to try it out.
DISCLAIMER: Before doing any of this stuff make sure you have the proper licenses, follow the applicable rules, are in a screen room, etc.
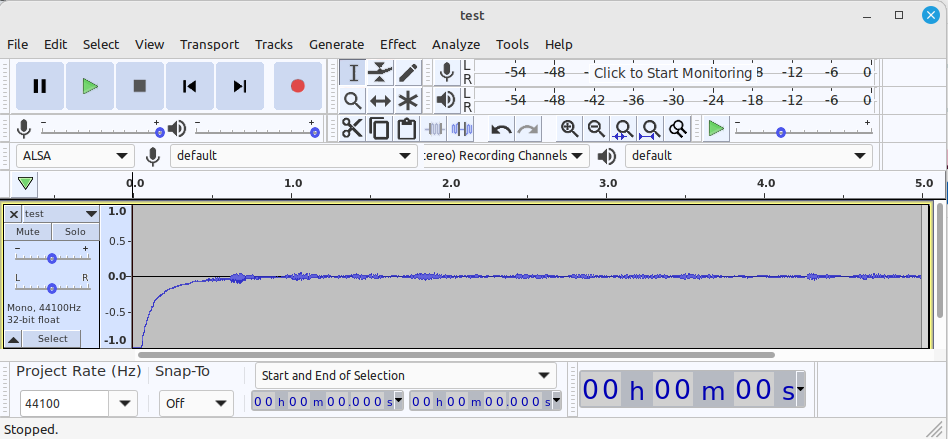
First I setup a linux laptop running a hackrf. I recorded a wav file of my voice:
arecord -d 5 -f S16_LE -r 44100 test.wav
This created a 5 second clip at a sampling rate of 44.1 kHz and saved it to a file called test.wav. I Mixed and rendered it to a single channel, made any edits, made sure it was set to 44,100 Hz, and then exported to a 16 bit PCM wav file called testDigital.wav.

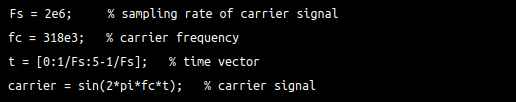
I then created a carrier signal using Octave.

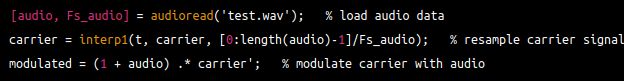
Next I modulated the carrier signal with the audio, also in Octave:

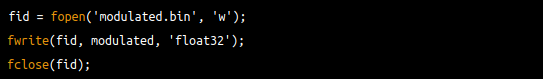
Finally I wrote the modulated signal to a binary file named modulated.bin using Octave:

Next I used hackrf_transfer to transmit the binary file on a frequency of 318kHz:
hackrf_transfer -t modulated.bin -f 318000 -R
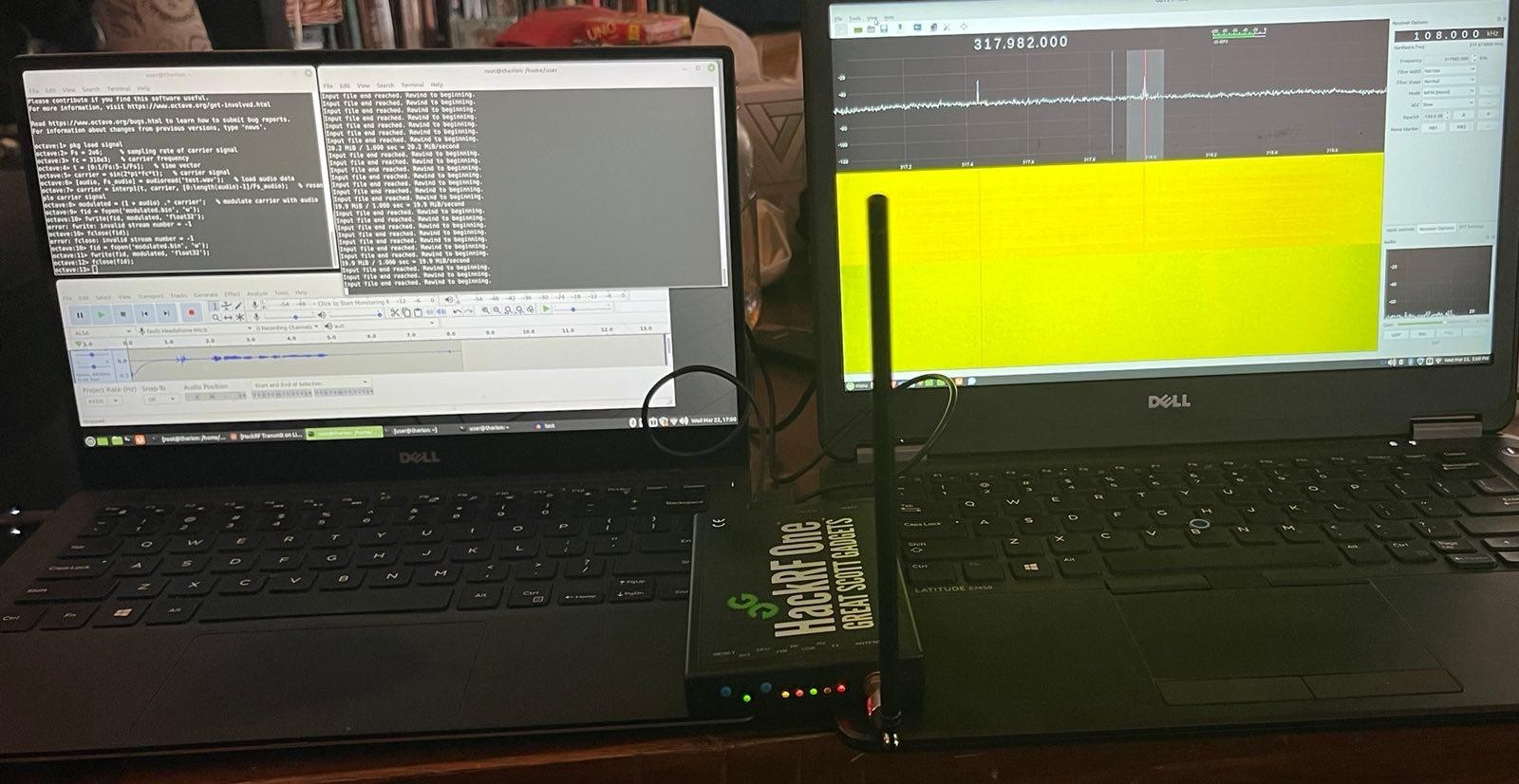
On a second laptop I setup a NESDR Smart SDR and ran Gqrx set to 318kHz in order to see and receive the signal. In the following image you can see the signal being transmitted through the hackrf with the computer on the left and then you can see the signal being received and seen in Gqrx with the computer on the right:

Next I setup the flipperzero to read and record the signal being transmitted:


Then I stopped transmitting from the hackrf and stopped recording with the flipperzero, and then had the flipperzero replay the signal:


Finally we can see on the NESDR Smart SDR the signal sent by the flipperzero:
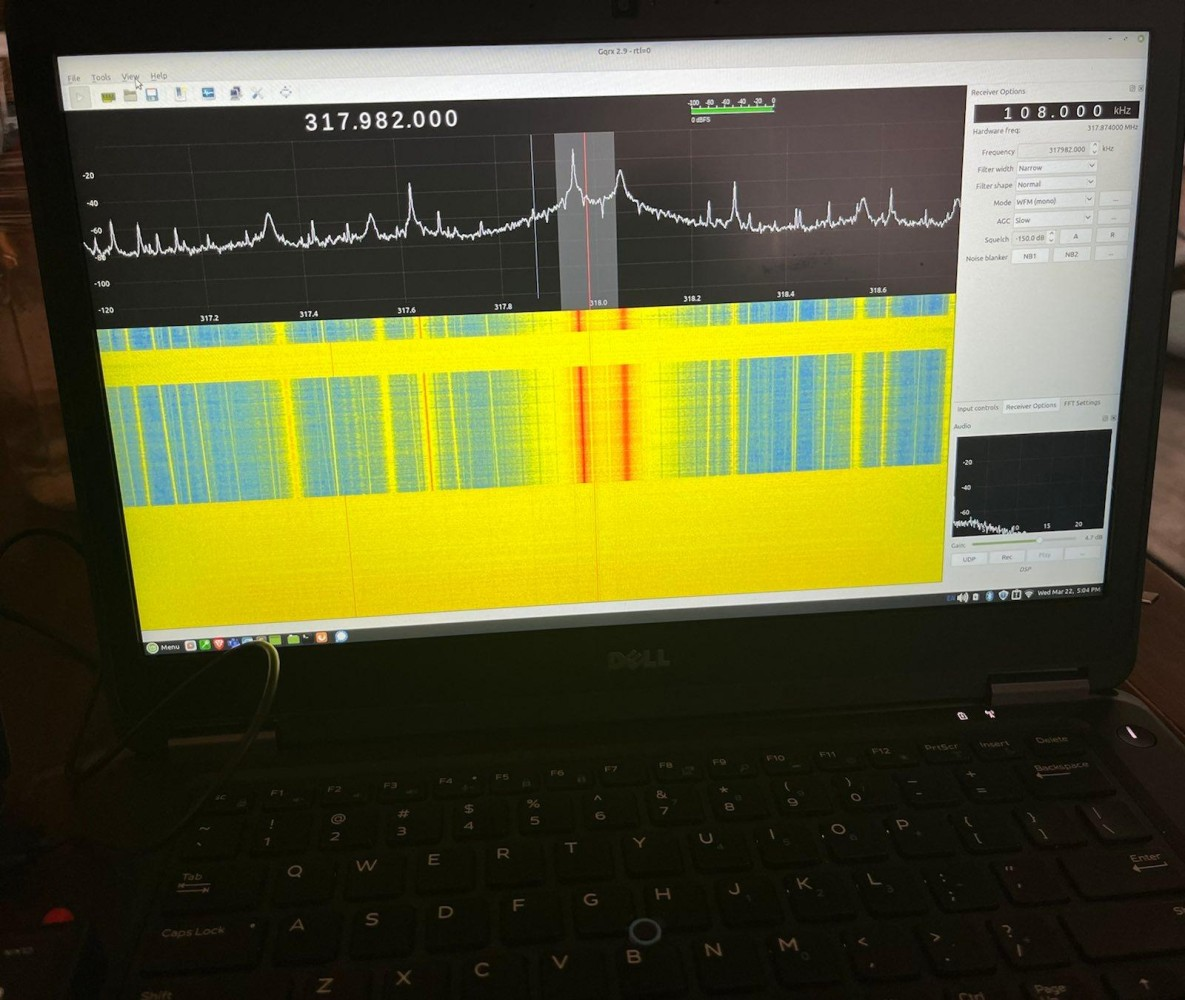

I need to play with different frequencies and devices but I believe the flipperzero can be used to steal, modify, and replay signals. I could imagine stealing a proximity badge, maybe vehicle entry, etc. with this device.
All in all a fun day.
Thanks for listening!
A.

