What I Have Learned - Part 8 Communicating

A major part of my career in security was learning how and why to communicate what I was working on. This had a major impact on my progression so I thought I would share some of what I learned here.
When I was working at Los Alamos I had a colleague who was a legitimate genius. He had a masters degree in Computer Science and understood so much about every aspect from coding to networking to databases, forensics, reverse engineering. He was more qualified and better skilled than I was in most areas.
However, I made more money, got more promotions, and generally a better work situation than him and it took me a little while to understand why. As it turns out, he didn't write very well and he didn't give talks on what he was working on. The simple aspect of communicating his talent was the only thing holding him back. In contrast:
- Every time I found a new vulnerability, approach to attacking systems, or reverse engineered a new APT sample, I would write and release a paper and give internal as well as external presentations about it.
- Human psychology tends to make people believe the person on the stage is an expert and an authority (even if that's not exactly true).
Speaking and publishing widened the network of people that knew who I was and what I was working on, which in turn generated more opportunities for conversation, connections, projects, and customers. You can be doing the most amazing work, but if you do it in a vacuum it doesn't matter to the world or to your career. (This is an ironic statement coming from me as 95% of what I'm doing now isn't communicated or shared)
Unfortunately for me I hate public speaking but I pushed through that and spoke constantly for almost 10 years. At one point I had the record for the most talks (5) in one week in Vegas (never again). This, in addition to stubborn persistence, is one of the core steps I took which enabled everything else that came later.
The second lesson I learned about communication was to simplify and tailor the message, and strategically consider the audience. Let me give an example.
The first public talk I gave was Defcon in around 2005. Here is an example slide from the talk:
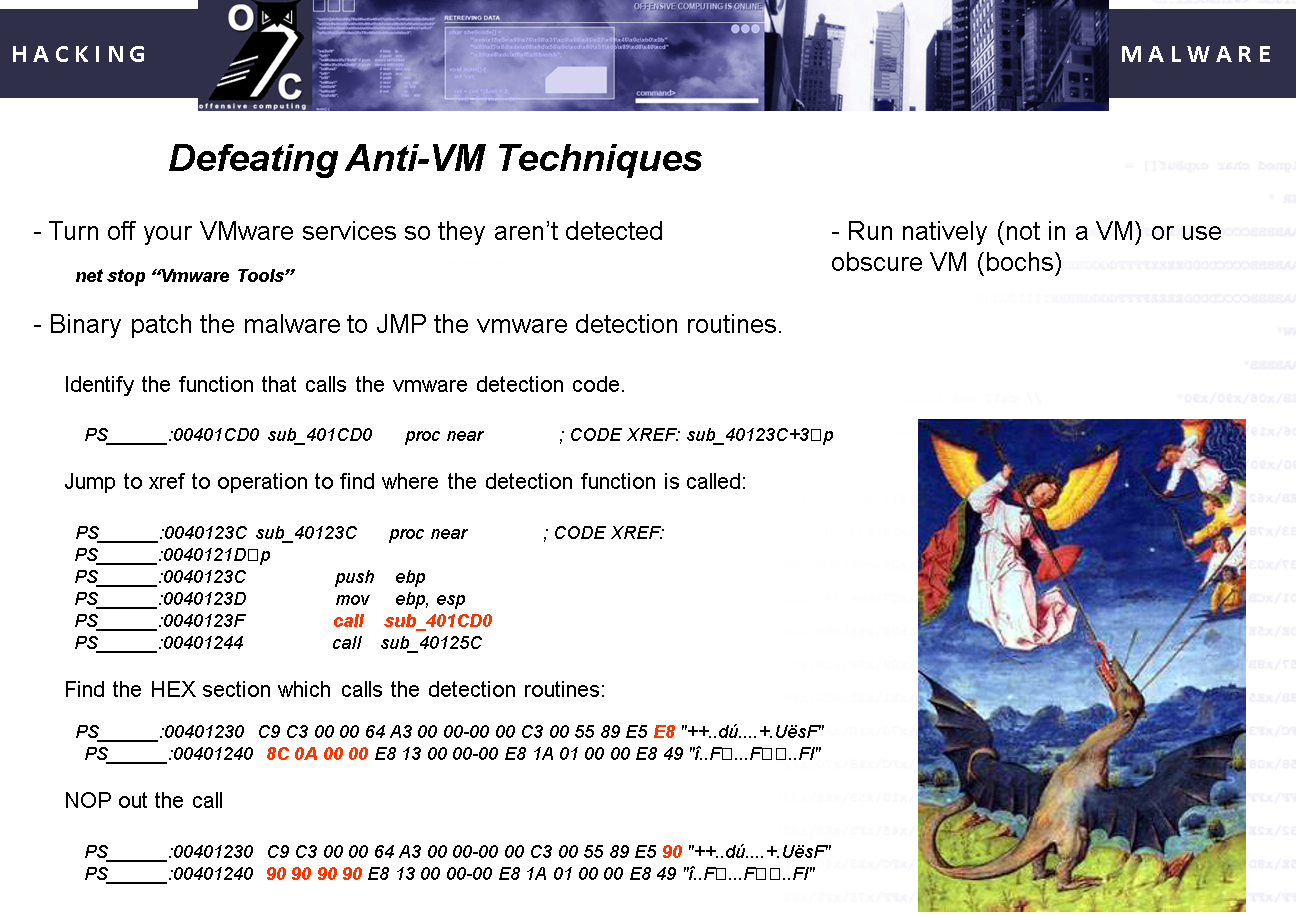

Now I understood a little about presenting because I included an image to draw and hold the audience attention, but look at the rest of the slide. It consists mainly of x86 Assembly and some hex code. This talk generated a bit of buzz and a lot of other researchers liked it, but to be honest the average audience member wasn't that into it. It was too abstract and technical and didn't convey a concept that they could take home and apply to their environments or jobs.
Here is a slide from the last major public talk I gave at BSides Las Vegas, don't remember the year but it was probably around 2014 or 2015.


This was a talk about the criminal blackhat community and the war they were waging on security researchers. The slides consisted mainly of funny, vivid, or shocking images with short, clear statements. I was conveying the vulnerability of the security community (I myself had been hacked by the ZF0 group) and some of the realities about the perception of big name speakers versus the reality. The presentation had 87 slides and only two of them had any code. Example:
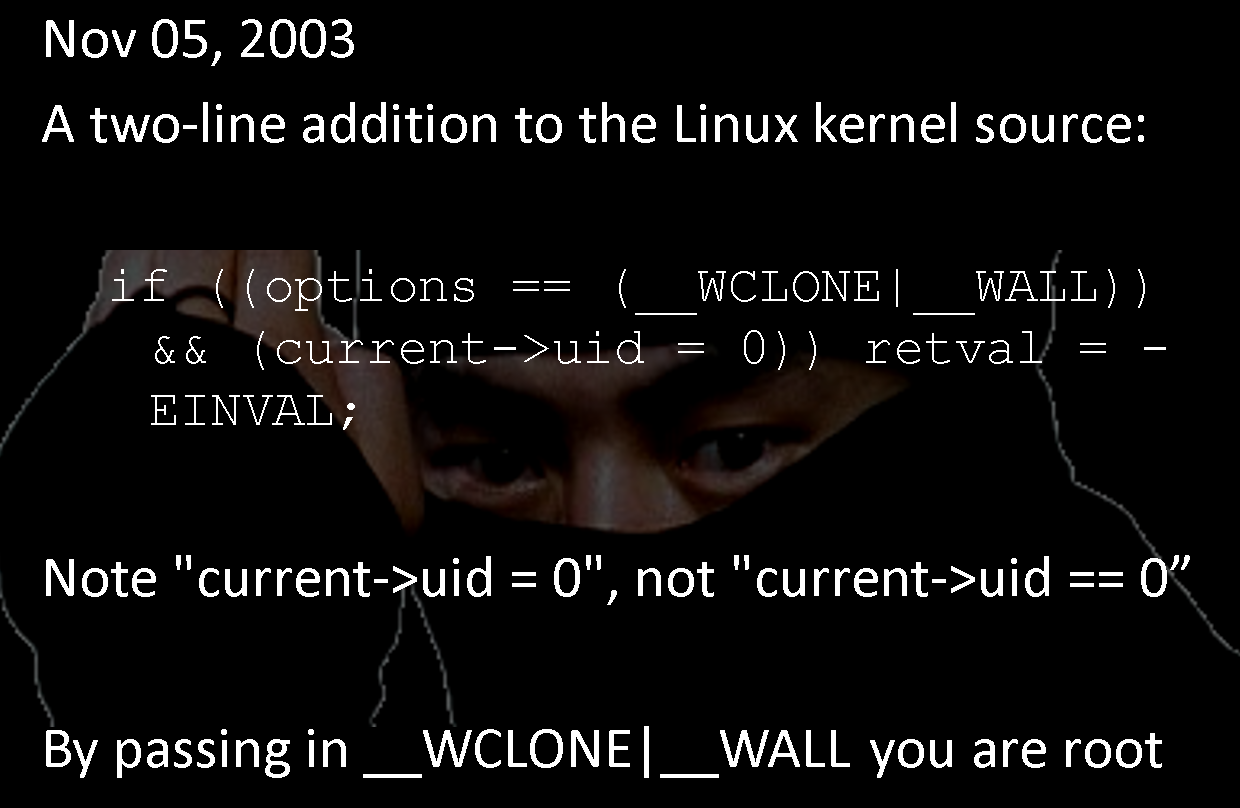

This generated a ton more interest than my first talk and was easy for people to understand.
The talk that generated the most impact was one I gave with H. D. Moore called Tactical Exploitation. It filled the big ballroom at Blackhat and people were spilling out into the hall. It felt like there were over 1000 people watching. (A lot of the draw was due to HD and Metasploit's fame at that time).
This was a talk about simple methods real world hackers used to infiltrate systems, mostly behaving like a malicious sysadmin. Other researchers didn't care that much about it, there were no interesting memory exploitation techniques, novel kernel rootkit approaches, or pages of assembly.
The public on the other hand was very into it and this allowed us to launch a training course based on it that ran for 7-10 years afterword's and generated tens of thousands of dollars in revenue.
What lead me to this change of approach was that I had a realization while watching an excellent talk by Joanna Rutkowska on very advanced rootkits.


The talk was intense, highly technical, and had page after page of code. Many of the ideas she talked about were revolutionary at that time. It was right at the edge of my ability to understand and keep up. At one point I looked around at the audience and noticed something. These were CISOs, system administrators, IT executives, people interested in getting into security. There was probably over 500 people there and 90% of them looked lost and checked out. None of the content presented was something they could take back and implement in their networks.
For me, as a fellow researcher, the talk was exciting and engaging, but I was never going to hire Joanna or buy any of her products at that time. I was a poor researcher myself who was going to go home and try to recreate what she presented and come up with my own rootkits.
The lightbulb went off. I wanted to reach the widest possible audience, especially those who would be likely to work with me in a commercial sense to expand my business and give me exposure to larger environments and other technologies. There is definitely a time and a place for pushing the limits and sharing cutting edge research to other researchers, but in order to achieve my goals I had to change my approach.
I started simplifying my message and focusing on topics that were of practical use to a majority of the audience. This doesn't mean I didn't continue to talk with other researchers and have my work critiqued by them, or that I wasn't working on more esoteric areas. I was simply strategic about what I shared and where.
Over the next several years I gave illustrated talks on:
- Common Vulnerabilities in International ERP systems
- APT Attacks Coming from China
- Tools for Conducting and Automating Phishing Attacks
- IoT and SCADA Attack Case Studies
- Approaches for Detecting and Attributing Web Based Attacks
While in the background I was working on:
- Mobile Device Post-Exploitation
- Memory Corruption Attacks Against Uncommon Systems (Vax, AS400, HPUX, etc.)
- Automated Reverse Engineering & Testing of Malware (Including Automated De-Obfuscation Using Instruction Injection and Dumping on Mem Write/Executes)
- Automated C2 Generation Across Multiple Platforms
- Hacking Avionics, Automotive, and Point of Sale Systems
The Takeaway
No matter how much you might hate it, developing your ability to communicate your work either through public speaking or writing is one of the most effective ways to accelerate your growth and advancement.
Being strategic about how you communicate and to who, focusing on the wider audience that provides a return rather than catering only to your peers, and simplifying your message can change the game.
Thanks for listening,
A.

